|
|
|
The human body produces and destroys 15 million blood cells every second.
Approximately 25% of all reported medication errors result from some kind of name confusion.
Thyroid conditions may make getting pregnant impossible.
The most common childhood diseases include croup, chickenpox, ear infections, flu, pneumonia, ringworm, respiratory syncytial virus, scabies, head lice, and asthma.
GI conditions that will keep you out of the U.S. armed services include ulcers, varices, fistulas, esophagitis, gastritis, congenital abnormalities, inflammatory bowel disease, enteritis, colitis, proctitis, duodenal diverticula, malabsorption syndromes, hepatitis, cirrhosis, cysts, abscesses, pancreatitis, polyps, certain hemorrhoids, splenomegaly, hernias, recent abdominal surgery, GI bypass or stomach stapling, and artificial GI openings.
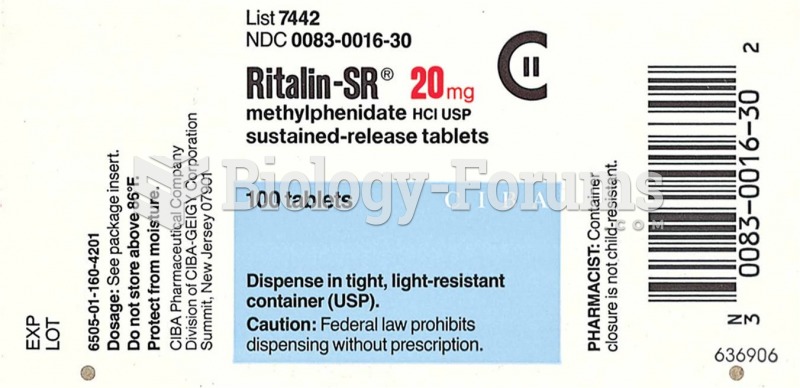 Examples of USP labels Source: Courtesy of Novartis Pharmaceuticals Corporation and Mallinckrodt Pha
Examples of USP labels Source: Courtesy of Novartis Pharmaceuticals Corporation and Mallinckrodt Pha
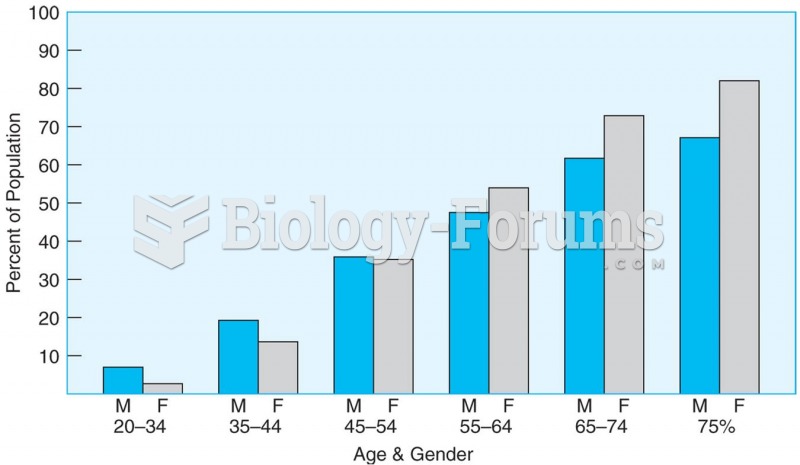 The proportion of men and women with elevated blood pressure or taking hypertension medication incre
The proportion of men and women with elevated blood pressure or taking hypertension medication incre