|
|
|
Did you know?
Asthma is the most common chronic childhood disease in the world. Most children who develop asthma have symptoms before they are 5 years old.
Did you know?
More than 4.4billion prescriptions were dispensed within the United States in 2016.
Did you know?
More than nineteen million Americans carry the factor V gene that causes blood clots, pulmonary embolism, and heart disease.
Did you know?
The human body produces and destroys 15 million blood cells every second.
Did you know?
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
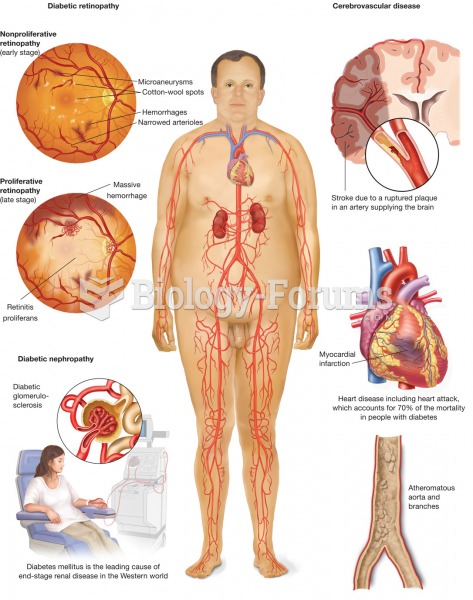 Diabetes mellitus. The metabolic disease diabetes mellitus, with symptoms of polydipsia, polyuria, a
Diabetes mellitus. The metabolic disease diabetes mellitus, with symptoms of polydipsia, polyuria, a
 The terrorist attack of September 11, 2001, is surely a defining event for the cohorts who experienc
The terrorist attack of September 11, 2001, is surely a defining event for the cohorts who experienc





