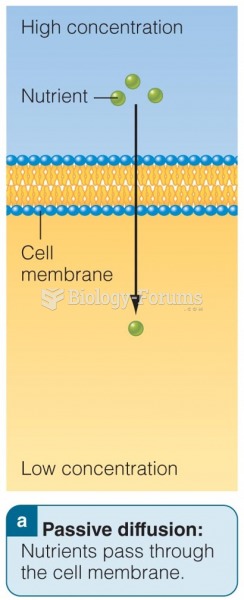
|
|
|
Stroke kills people from all ethnic backgrounds, but the people at highest risk for fatal strokes are: black men, black women, Asian men, white men, and white women.
GI conditions that will keep you out of the U.S. armed services include ulcers, varices, fistulas, esophagitis, gastritis, congenital abnormalities, inflammatory bowel disease, enteritis, colitis, proctitis, duodenal diverticula, malabsorption syndromes, hepatitis, cirrhosis, cysts, abscesses, pancreatitis, polyps, certain hemorrhoids, splenomegaly, hernias, recent abdominal surgery, GI bypass or stomach stapling, and artificial GI openings.
Common abbreviations that cause medication errors include U (unit), mg (milligram), QD (every day), SC (subcutaneous), TIW (three times per week), D/C (discharge or discontinue), HS (at bedtime or "hours of sleep"), cc (cubic centimeters), and AU (each ear).
Women are two-thirds more likely than men to develop irritable bowel syndrome. This may be attributable to hormonal changes related to their menstrual cycles.
A recent study has found that following a diet rich in berries may slow down the aging process of the brain. This diet apparently helps to keep dopamine levels much higher than are seen in normal individuals who do not eat berries as a regular part of their diet as they enter their later years.