|
|
|
The use of salicylates dates back 2,500 years to Hippocrates’s recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
Autoimmune diseases occur when the immune system destroys its own healthy tissues. When this occurs, white blood cells cannot distinguish between pathogens and normal cells.
Before a vaccine is licensed in the USA, the Food and Drug Administration (FDA) reviews it for safety and effectiveness. The CDC then reviews all studies again, as well as the American Academy of Pediatrics and the American Academy of Family Physicians. Every lot of vaccine is tested before administration to the public, and the FDA regularly inspects vaccine manufacturers' facilities.
The toxic levels for lithium carbonate are close to the therapeutic levels. Signs of toxicity include fine hand tremor, polyuria, mild thirst, nausea, general discomfort, diarrhea, vomiting, drowsiness, muscular weakness, lack of coordination, ataxia, giddiness, tinnitus, and blurred vision.
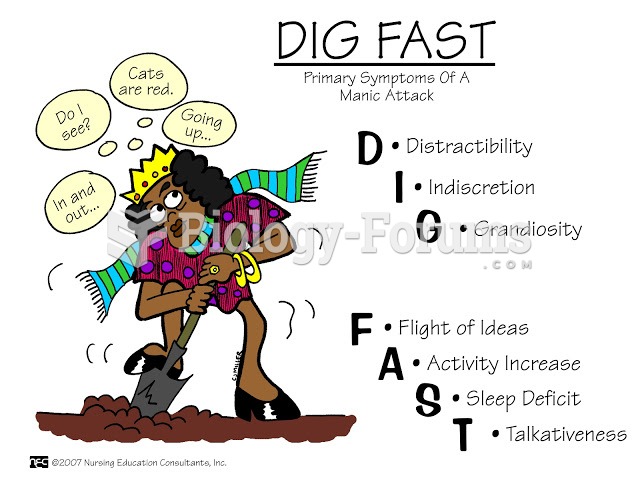
The highest suicide rate in the United States is among people ages 65 years and older. Almost 15% of people in this age group commit suicide every year.