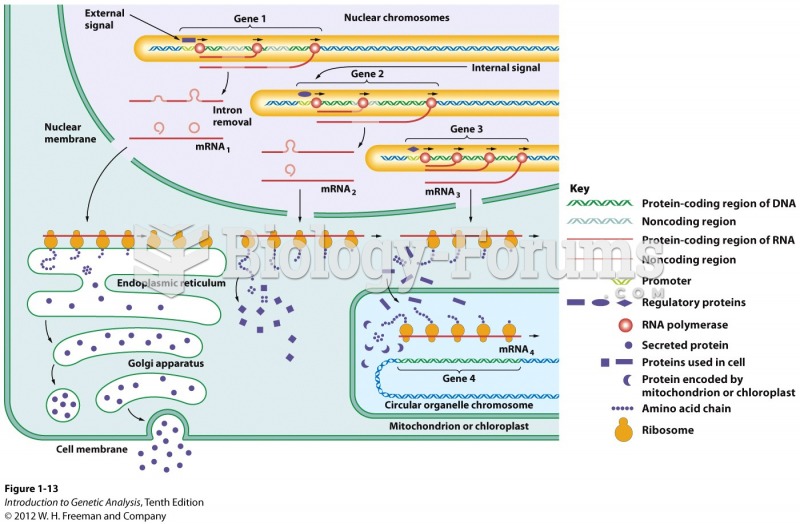
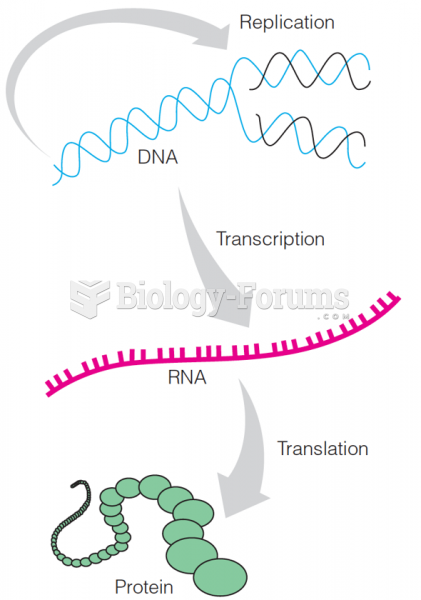
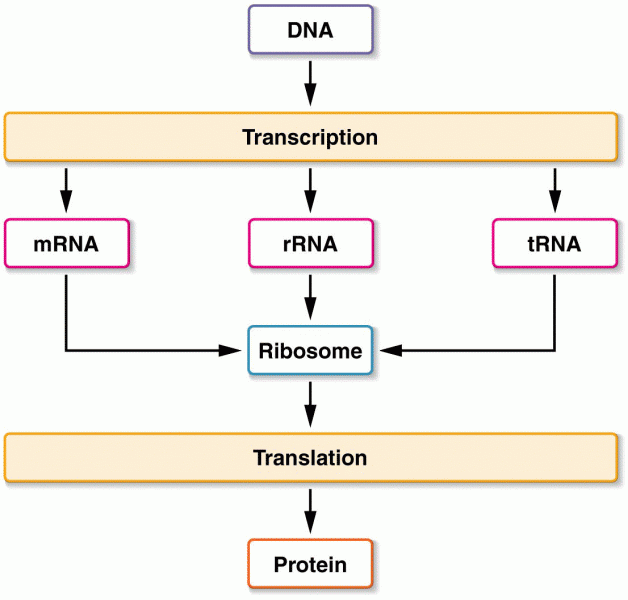
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Thyroid conditions may make getting pregnant impossible.
Did you know?
Not getting enough sleep can greatly weaken the immune system. Lack of sleep makes you more likely to catch a cold, or more difficult to fight off an infection.
Did you know?
Only one in 10 cancer deaths is caused by the primary tumor. The vast majority of cancer mortality is caused by cells breaking away from the main tumor and metastasizing to other parts of the body, such as the brain, bones, or liver.
Did you know?
Of the estimated 2 million heroin users in the United States, 600,000–800,000 are considered hardcore addicts. Heroin addiction is considered to be one of the hardest addictions to recover from.
Did you know?
Medication errors are more common among seriously ill patients than with those with minor conditions.