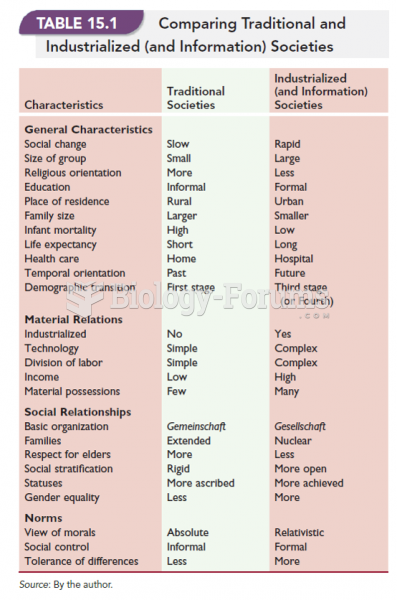
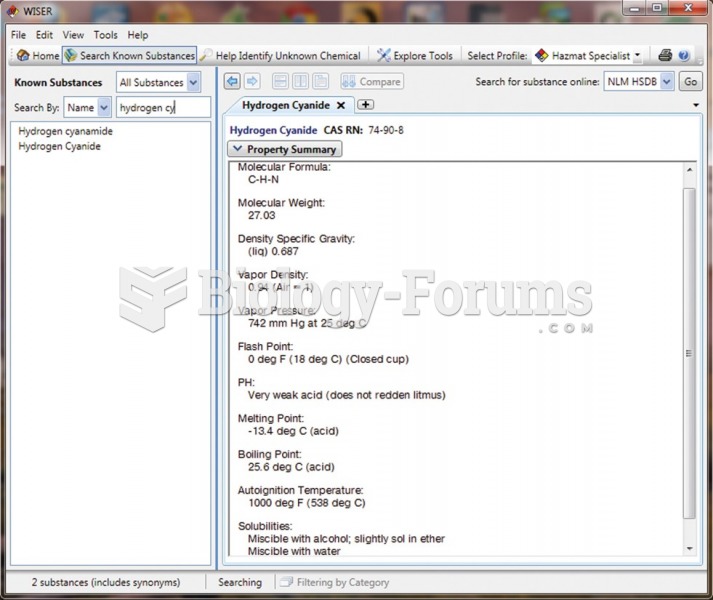
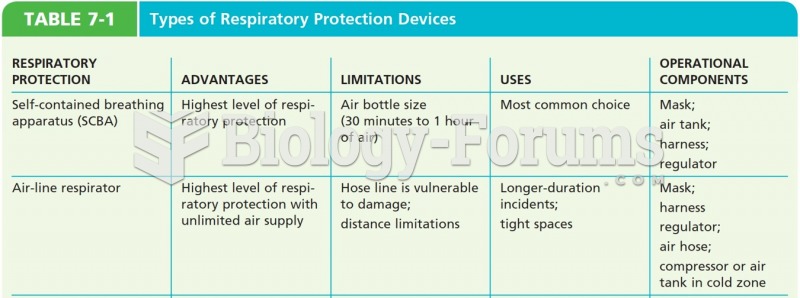
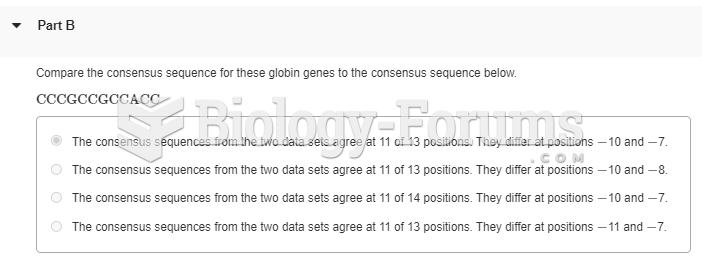
|
|
|
Hippocrates noted that blood separates into four differently colored liquids when removed from the body and examined: a pure red liquid mixed with white liquid material with a yellow-colored froth at the top and a black substance that settles underneath; he named these the four humors (for blood, phlegm, yellow bile, and black bile).
The immune system needs 9.5 hours of sleep in total darkness to recharge completely.
The longest a person has survived after a heart transplant is 24 years.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
Throughout history, plants containing cardiac steroids have been used as heart drugs and as poisons (e.g., in arrows used in combat), emetics, and diuretics.