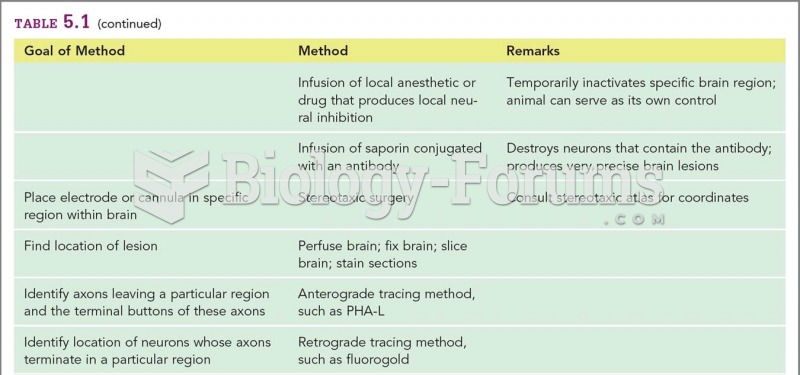
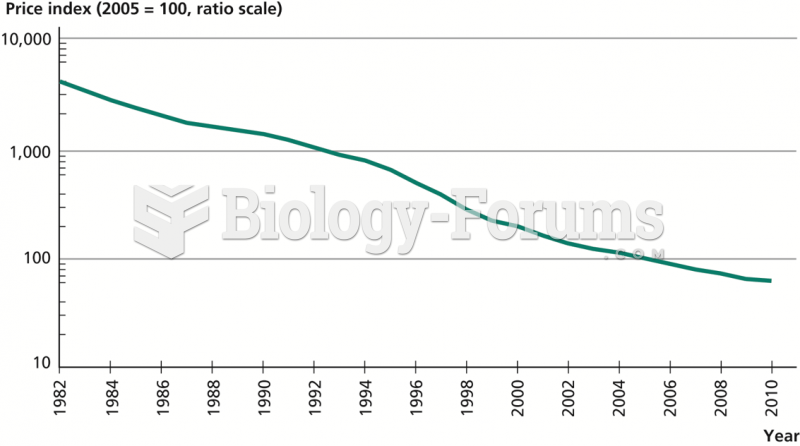
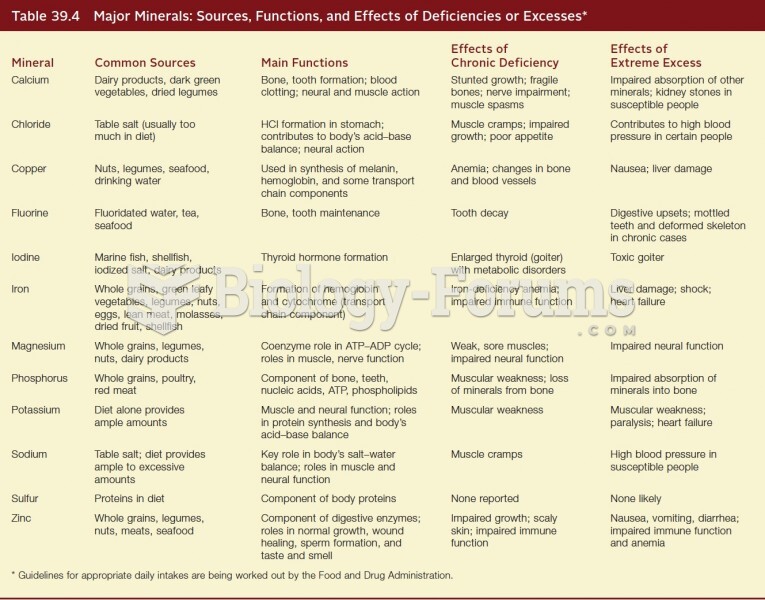
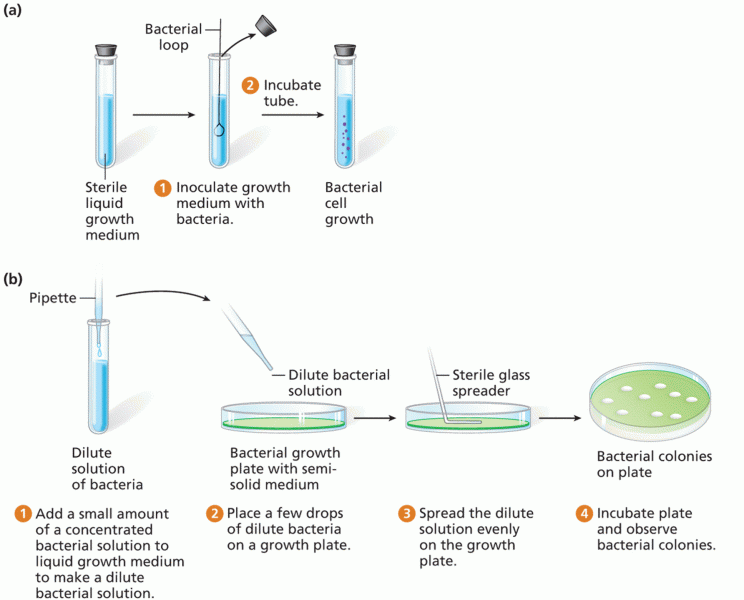
|
|
|
Did you know?
In the United States, there is a birth every 8 seconds, according to the U.S. Census Bureau's Population Clock.
Did you know?
Illicit drug use costs the United States approximately $181 billion every year.
Did you know?
Recent studies have shown that the number of medication errors increases in relation to the number of orders that are verified per pharmacist, per work shift.
Did you know?
Vital signs (blood pressure, temperature, pulse rate, respiration rate) should be taken before any drug administration. Patients should be informed not to use tobacco or caffeine at least 30 minutes before their appointment.
Did you know?
Nitroglycerin is used to alleviate various heart-related conditions, and it is also the chief component of dynamite (but mixed in a solid clay base to stabilize it).