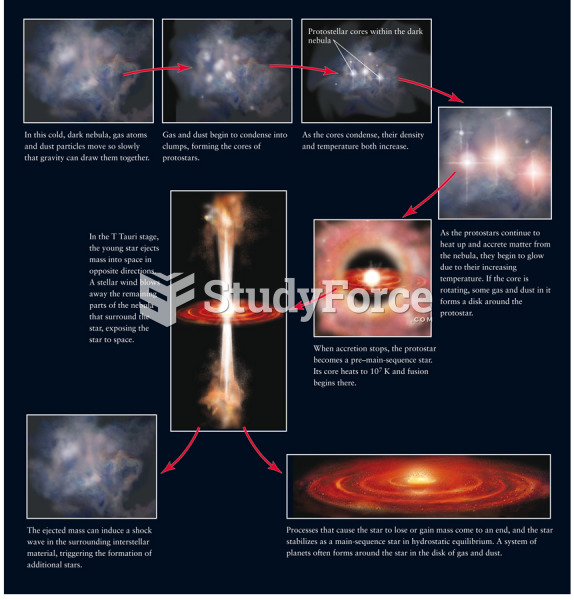
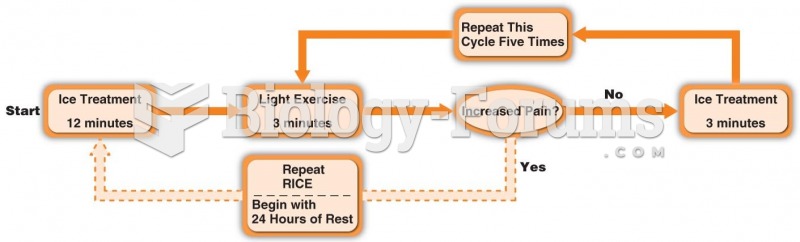
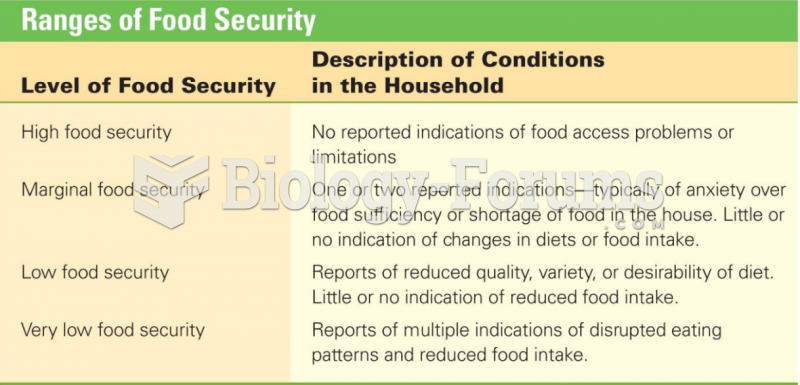
|
|
|
If all the neurons in the human body were lined up, they would stretch more than 600 miles.
An identified risk factor for osteoporosis is the intake of excessive amounts of vitamin A. Dietary intake of approximately double the recommended daily amount of vitamin A, by women, has been shown to reduce bone mineral density and increase the chances for hip fractures compared with women who consumed the recommended daily amount (or less) of vitamin A.
Asthma is the most common chronic childhood disease in the world. Most children who develop asthma have symptoms before they are 5 years old.
The horizontal fraction bar was introduced by the Arabs.
The toxic levels for lithium carbonate are close to the therapeutic levels. Signs of toxicity include fine hand tremor, polyuria, mild thirst, nausea, general discomfort, diarrhea, vomiting, drowsiness, muscular weakness, lack of coordination, ataxia, giddiness, tinnitus, and blurred vision.