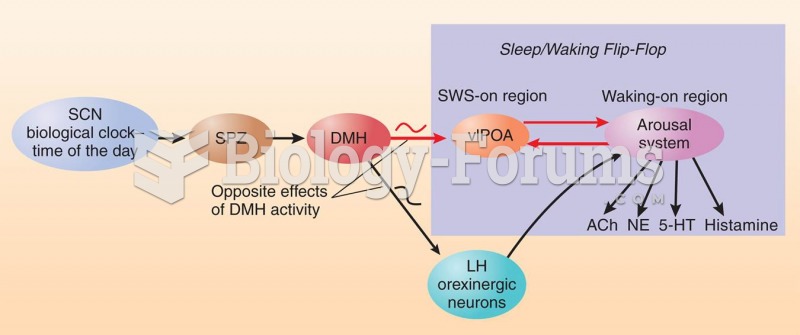
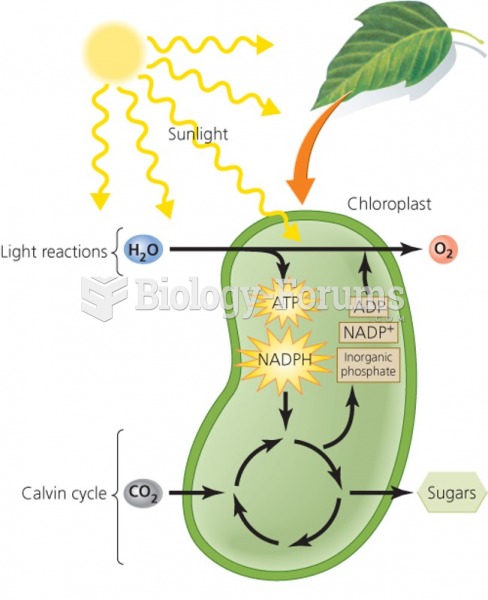
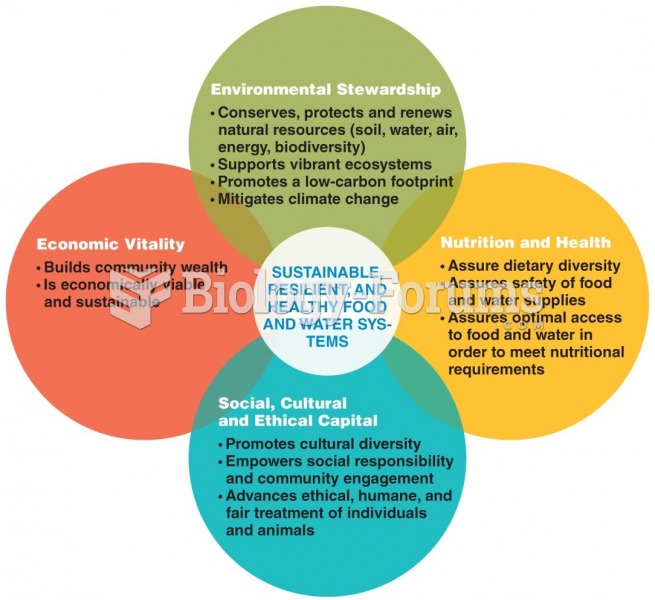
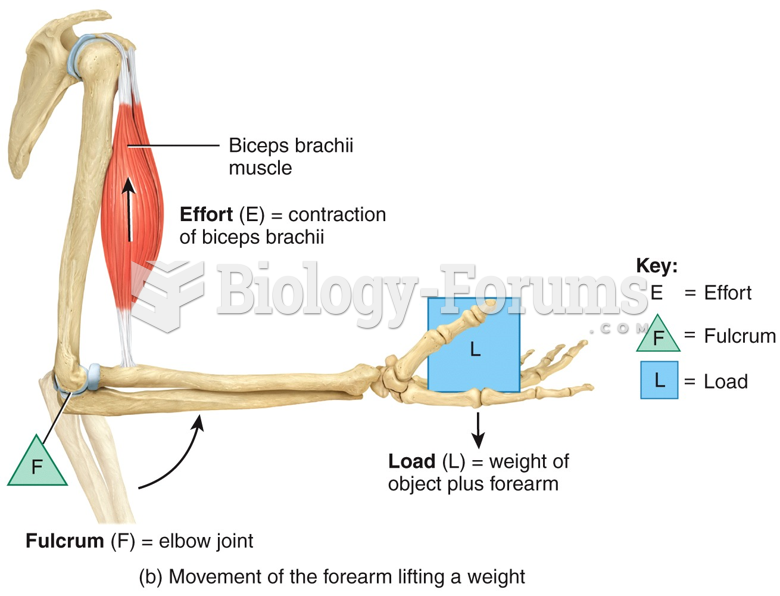
|
|
|
In 2012, nearly 24 milliion Americans, aged 12 and older, had abused an illicit drug, according to the National Institute on Drug Abuse (NIDA).
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.
Certain chemicals, after ingestion, can be converted by the body into cyanide. Most of these chemicals have been removed from the market, but some old nail polish remover, solvents, and plastics manufacturing solutions can contain these substances.
Adult head lice are gray, about ? inch long, and often have a tiny dot on their backs. A female can lay between 50 and 150 eggs within the several weeks that she is alive. They feed on human blood.
Urine turns bright yellow if larger than normal amounts of certain substances are consumed; one of these substances is asparagus.