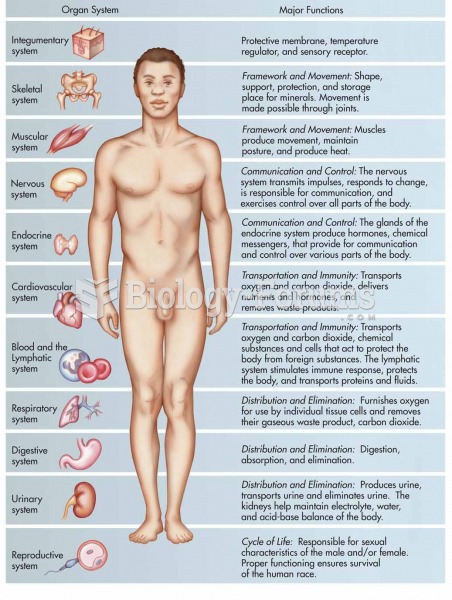
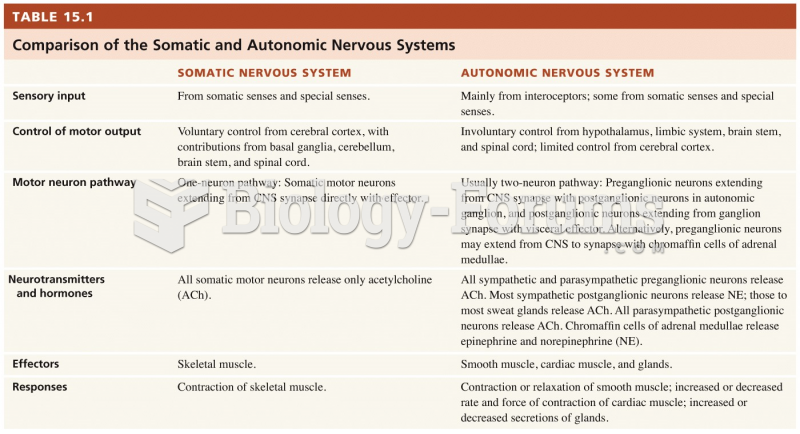
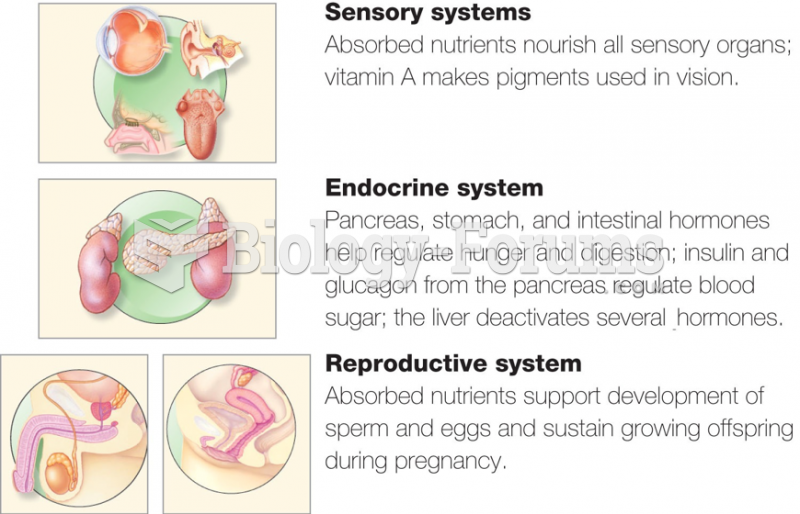
|
|
|
Oxytocin is recommended only for pregnancies that have a medical reason for inducing labor (such as eclampsia) and is not recommended for elective procedures or for making the birthing process more convenient.
By definition, when a medication is administered intravenously, its bioavailability is 100%.
The National Institutes of Health have supported research into acupuncture. This has shown that acupuncture significantly reduced pain associated with osteoarthritis of the knee, when used as a complement to conventional therapies.
The familiar sounds of your heart are made by the heart's valves as they open and close.
The cure for trichomoniasis is easy as long as the patient does not drink alcoholic beverages for 24 hours. Just a single dose of medication is needed to rid the body of the disease. However, without proper precautions, an individual may contract the disease repeatedly. In fact, most people develop trichomoniasis again within three months of their last treatment.