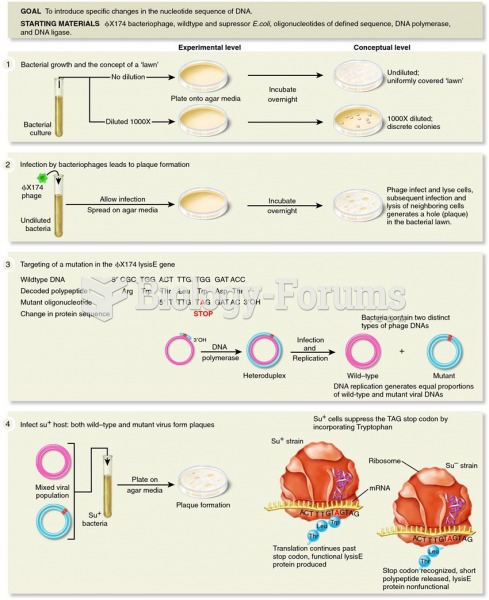
|
|
|
Intradermal injections are somewhat difficult to correctly administer because the skin layers are so thin that it is easy to accidentally punch through to the deeper subcutaneous layer.
To prove that stomach ulcers were caused by bacteria and not by stress, a researcher consumed an entire laboratory beaker full of bacterial culture. After this, he did indeed develop stomach ulcers, and won the Nobel Prize for his discovery.
Disorders that may affect pharmacodynamics include genetic mutations, malnutrition, thyrotoxicosis, myasthenia gravis, Parkinson's disease, and certain forms of insulin-resistant diabetes mellitus.
About 3.2 billion people, nearly half the world population, are at risk for malaria. In 2015, there are about 214 million malaria cases and an estimated 438,000 malaria deaths.
Though Candida and Aspergillus species are the most common fungal pathogens causing invasive fungal disease in the immunocompromised, infections due to previously uncommon hyaline and dematiaceous filamentous fungi are occurring more often today. Rare fungal infections, once accurately diagnosed, may require surgical debridement, immunotherapy, and newer antifungals used singly or in combination with older antifungals, on a case-by-case basis.