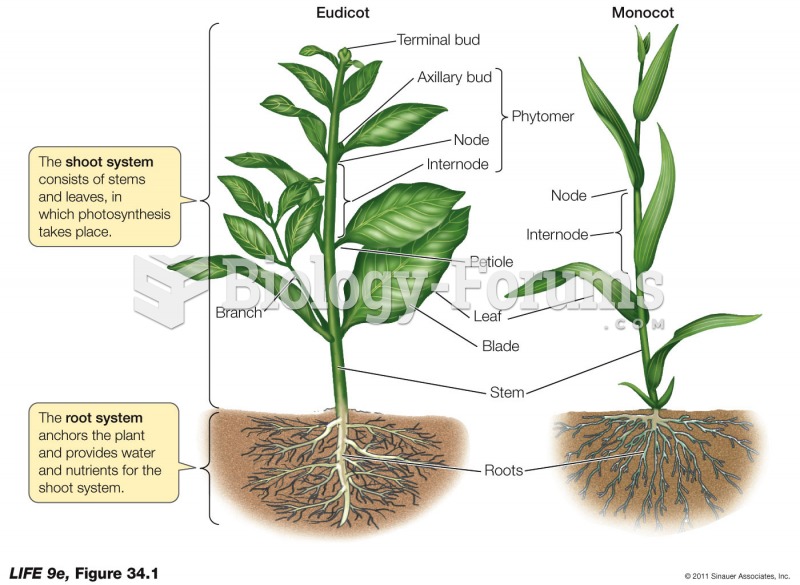
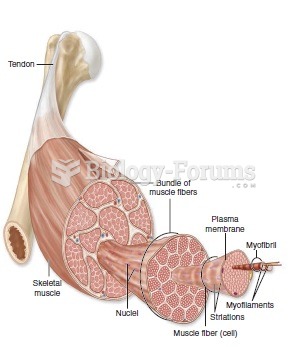
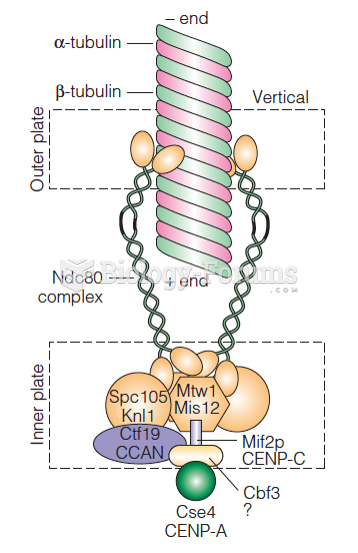
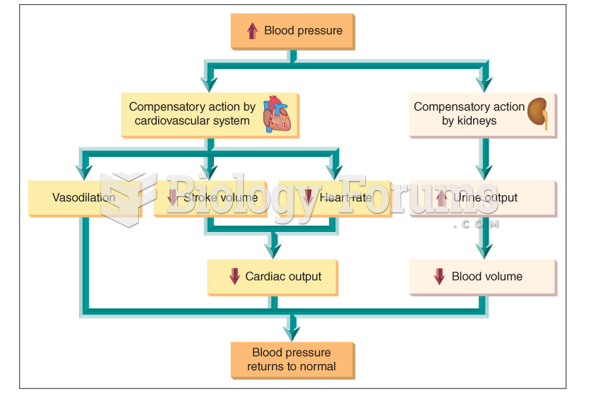
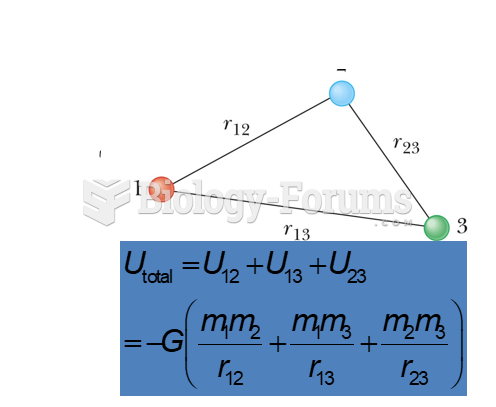
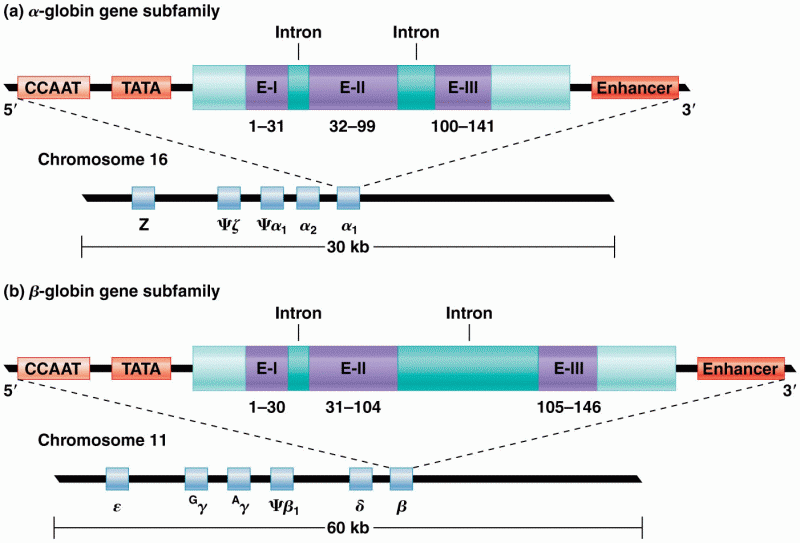
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
This year, an estimated 1.4 million Americans will have a new or recurrent heart attack.
Did you know?
In most cases, kidneys can recover from almost complete loss of function, such as in acute kidney (renal) failure.
Did you know?
Fungal nail infections account for up to 30% of all skin infections. They affect 5% of the general population—mostly people over the age of 70.
Did you know?
The calories found in one piece of cherry cheesecake could light a 60-watt light bulb for 1.5 hours.
Did you know?
The average human gut is home to perhaps 500 to 1,000 different species of bacteria.