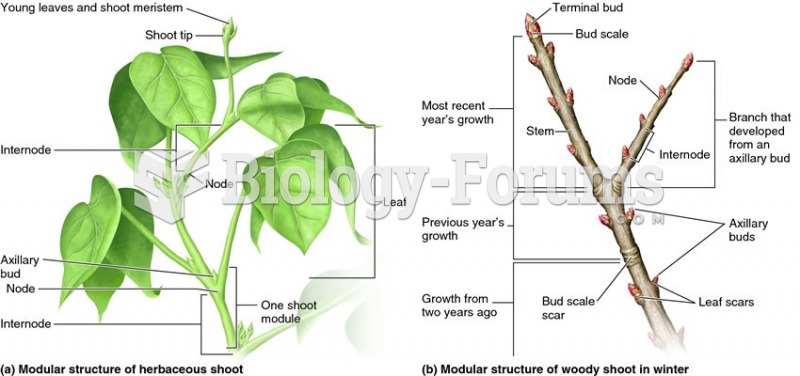
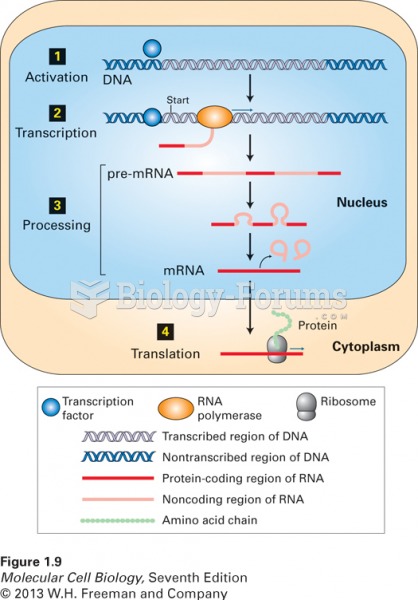
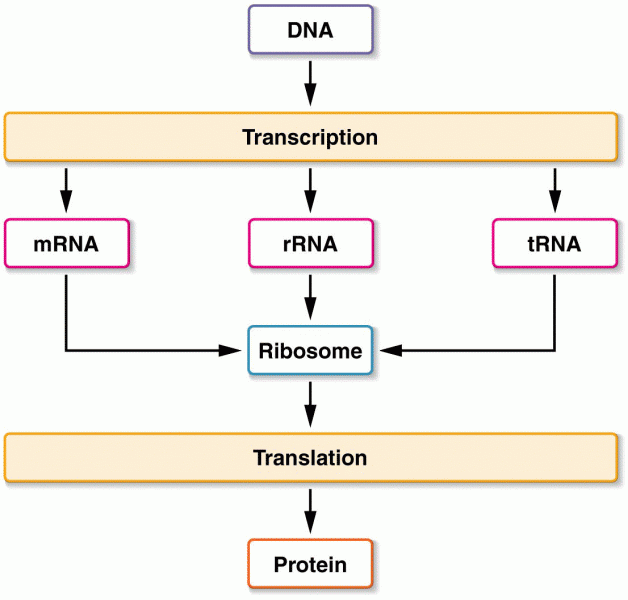
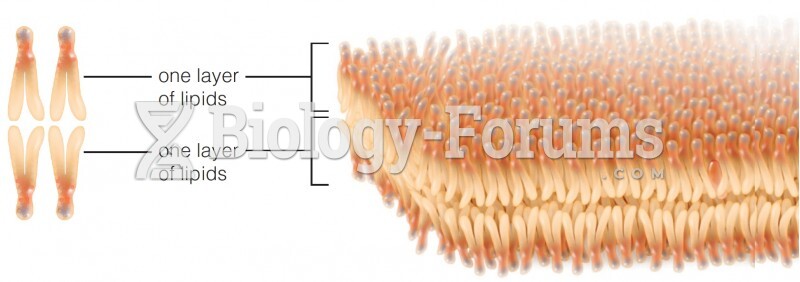
|
|
|
Did you know?
Vaccines prevent between 2.5 and 4 million deaths every year.
Did you know?
It is believed that humans initially contracted crabs from gorillas about 3 million years ago from either sleeping in gorilla nests or eating the apes.
Did you know?
Patients who have been on total parenteral nutrition for more than a few days may need to have foods gradually reintroduced to give the digestive tract time to start working again.
Did you know?
Most fungi that pathogenically affect humans live in soil. If a person is not healthy, has an open wound, or is immunocompromised, a fungal infection can be very aggressive.
Did you know?
More than 34,000 trademarked medication names and more than 10,000 generic medication names are in use in the United States.