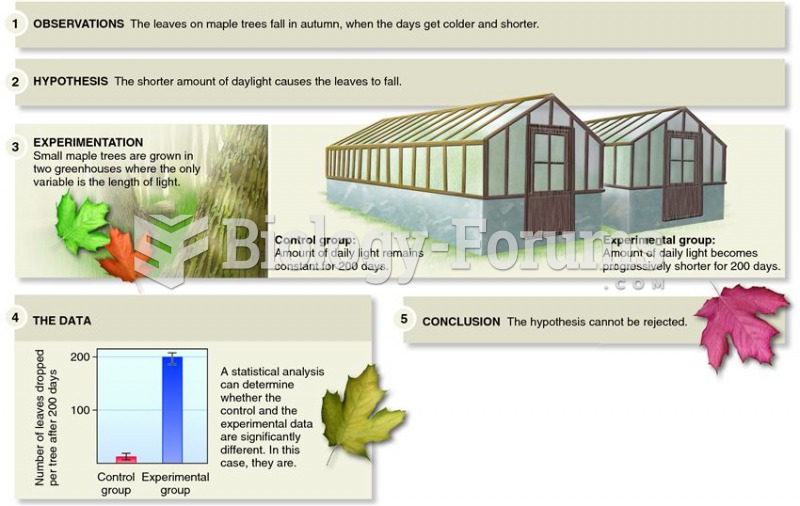
|
|
|
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
Cyanide works by making the human body unable to use oxygen.
In the United States, there is a birth every 8 seconds, according to the U.S. Census Bureau's Population Clock.
Cutaneous mucormycosis is a rare fungal infection that has been fatal in at least 29% of cases, and in as many as 83% of cases, depending on the patient's health prior to infection. It has occurred often after natural disasters such as tornados, and early treatment is essential.
Cancer has been around as long as humankind, but only in the second half of the twentieth century did the number of cancer cases explode.