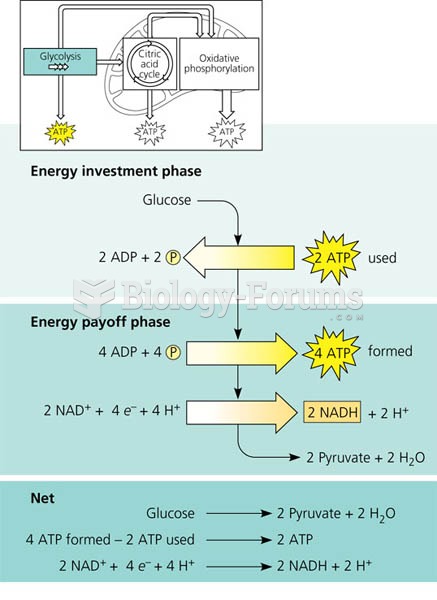
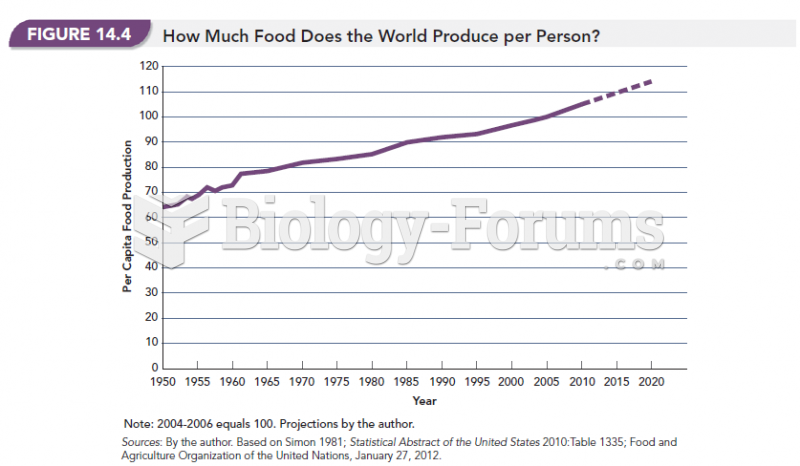
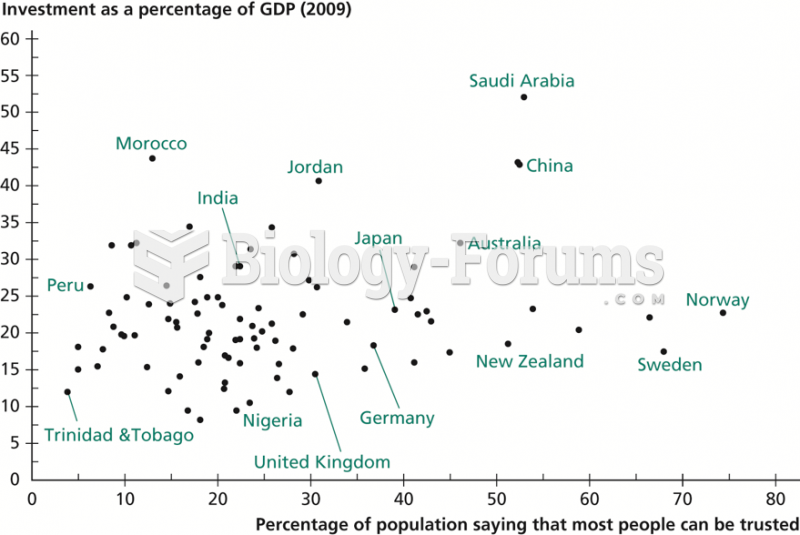
|
|
|
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
In women, pharmacodynamic differences include increased sensitivity to (and increased effectiveness of) beta-blockers, opioids, selective serotonin reuptake inhibitors, and typical antipsychotics.
Patients who have been on total parenteral nutrition for more than a few days may need to have foods gradually reintroduced to give the digestive tract time to start working again.
Interferon was scarce and expensive until 1980, when the interferon gene was inserted into bacteria using recombinant DNA technology, allowing for mass cultivation and purification from bacterial cultures.
The Food and Drug Administration has approved Risperdal, an adult antipsychotic drug, for the symptomatic treatment of irritability in children and adolescents with autism. The approval is the first for the use of a drug to treat behaviors associated with autism in children. These behaviors are included under the general heading of irritability and include aggression, deliberate self-injury, and temper tantrums.