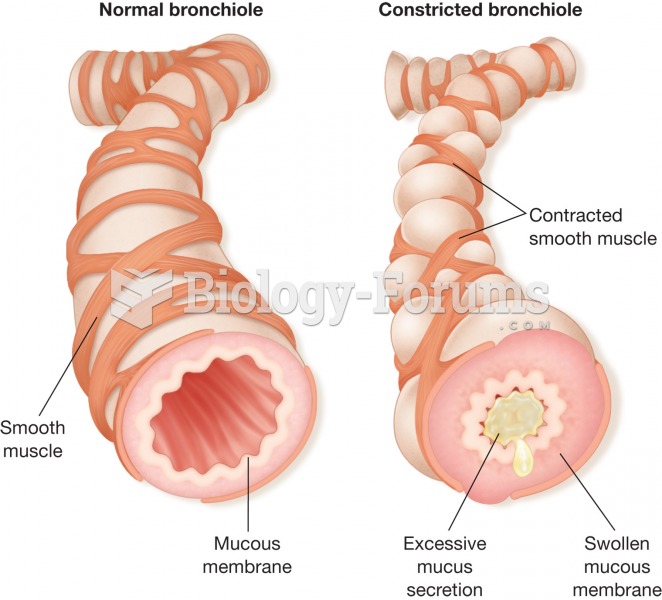
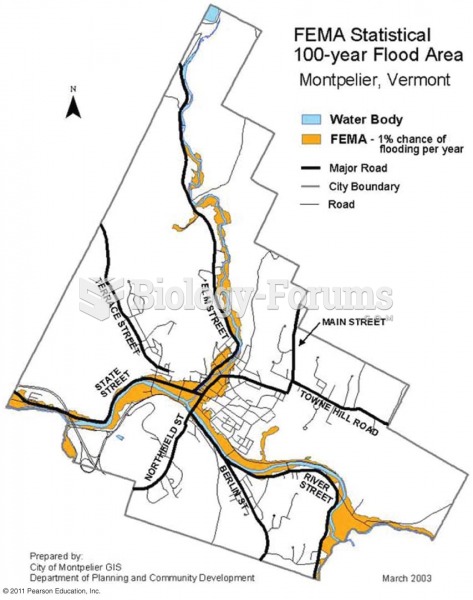
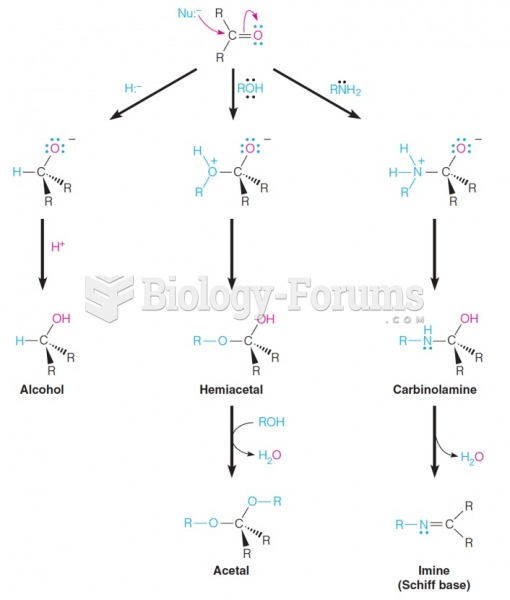
|
|
|
Adult head lice are gray, about ? inch long, and often have a tiny dot on their backs. A female can lay between 50 and 150 eggs within the several weeks that she is alive. They feed on human blood.
Children of people with alcoholism are more inclined to drink alcohol or use hard drugs. In fact, they are 400 times more likely to use hard drugs than those who do not have a family history of alcohol addiction.
Signs and symptoms of a drug overdose include losing consciousness, fever or sweating, breathing problems, abnormal pulse, and changes in skin color.
There are 60,000 miles of blood vessels in every adult human.
Giardia is one of the most common intestinal parasites worldwide, and infects up to 20% of the world population, mostly in poorer countries with inadequate sanitation. Infections are most common in children, though chronic Giardia is more common in adults.