|
|
|
Vital signs (blood pressure, temperature, pulse rate, respiration rate) should be taken before any drug administration. Patients should be informed not to use tobacco or caffeine at least 30 minutes before their appointment.
Illness; diuretics; laxative abuse; hot weather; exercise; sweating; caffeine; alcoholic beverages; starvation diets; inadequate carbohydrate consumption; and diets high in protein, salt, or fiber can cause people to become dehydrated.
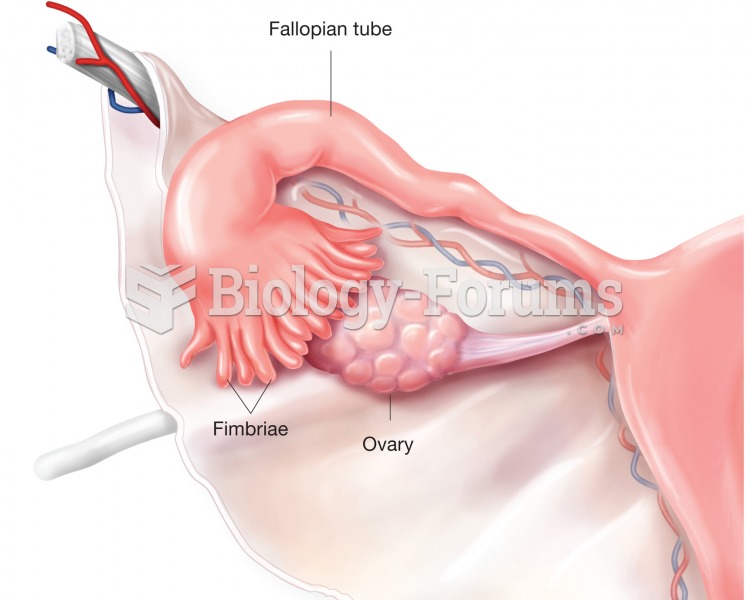
Women are two-thirds more likely than men to develop irritable bowel syndrome. This may be attributable to hormonal changes related to their menstrual cycles.
The oldest recorded age was 122. Madame Jeanne Calment was born in France in 1875 and died in 1997. She was a vegetarian and loved olive oil, port wine, and chocolate.
Atropine, along with scopolamine and hyoscyamine, is found in the Datura stramonium plant, which gives hallucinogenic effects and is also known as locoweed.