|
|
|
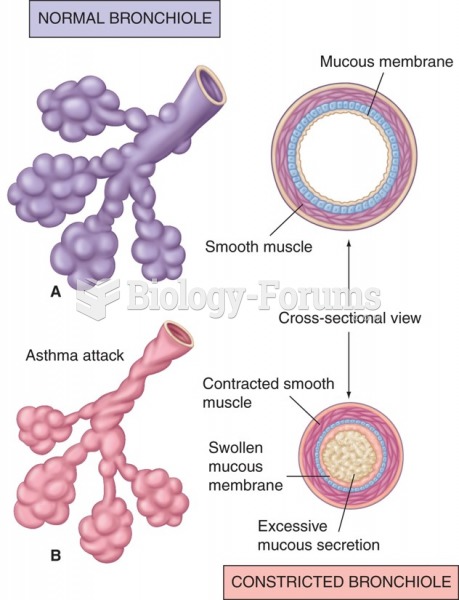
Asthma cases in Americans are about 75% higher today than they were in 1980.
Patients who have undergone chemotherapy for the treatment of cancer often complain of a lack of mental focus; memory loss; and a general diminution in abilities such as multitasking, attention span, and general mental agility.
Most women experience menopause in their 50s. However, in 1994, an Italian woman gave birth to a baby boy when she was 61 years old.
Walt Disney helped combat malaria by making an animated film in 1943 called The Winged Scourge. This short film starred the seven dwarfs and taught children that mosquitos transmit malaria, which is a very bad disease. It advocated the killing of mosquitos to stop the disease.
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.