|
|
|
According to the American College of Allergy, Asthma & Immunology, more than 50 million Americans have some kind of food allergy. Food allergies affect between 4 and 6% of children, and 4% of adults, according to the CDC. The most common food allergies include shellfish, peanuts, walnuts, fish, eggs, milk, and soy.
The cure for trichomoniasis is easy as long as the patient does not drink alcoholic beverages for 24 hours. Just a single dose of medication is needed to rid the body of the disease. However, without proper precautions, an individual may contract the disease repeatedly. In fact, most people develop trichomoniasis again within three months of their last treatment.
It is believed that humans initially contracted crabs from gorillas about 3 million years ago from either sleeping in gorilla nests or eating the apes.
All adverse reactions are commonly charted in red ink in the patient's record and usually are noted on the front of the chart. Failure to follow correct documentation procedures may result in malpractice lawsuits.
Multiple sclerosis is a condition wherein the body's nervous system is weakened by an autoimmune reaction that attacks the myelin sheaths of neurons.
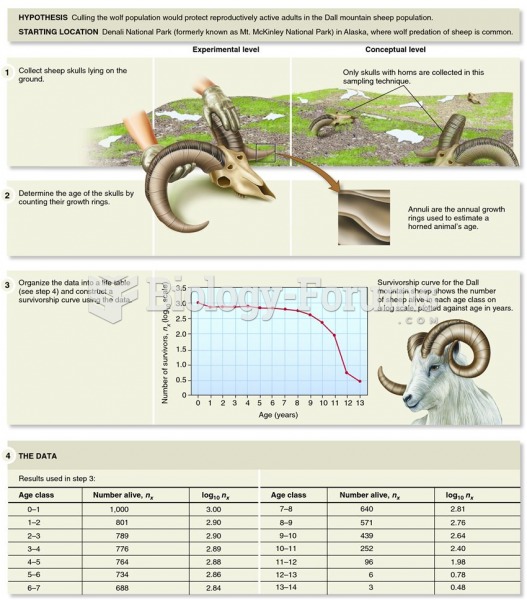 Examining the survivorship curve of a Dall mountain sheep population reveals information on the caus
Examining the survivorship curve of a Dall mountain sheep population reveals information on the caus
 Examining the survivorship curve of a Dall mountain sheep population reveals information on the caus
Examining the survivorship curve of a Dall mountain sheep population reveals information on the caus