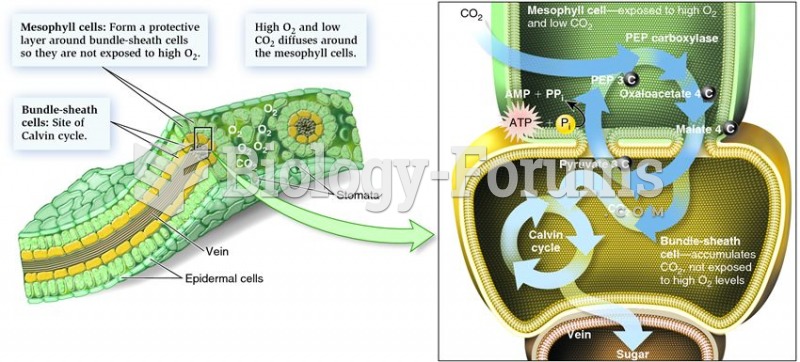
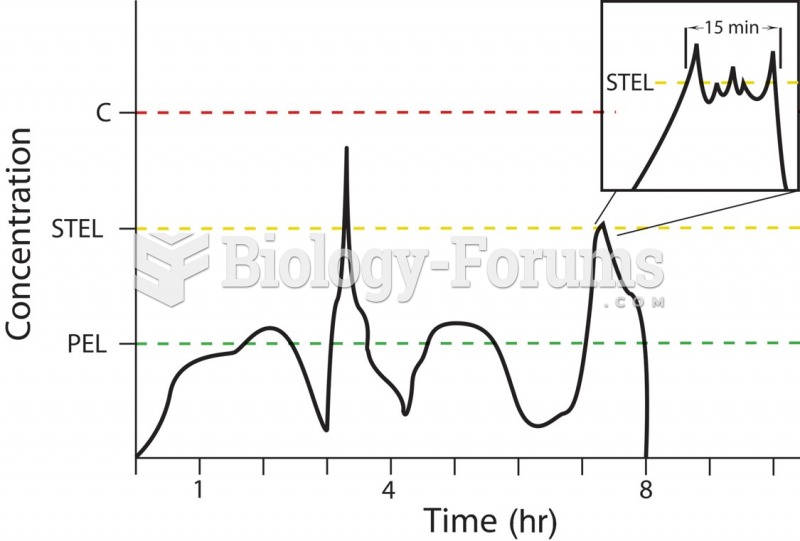
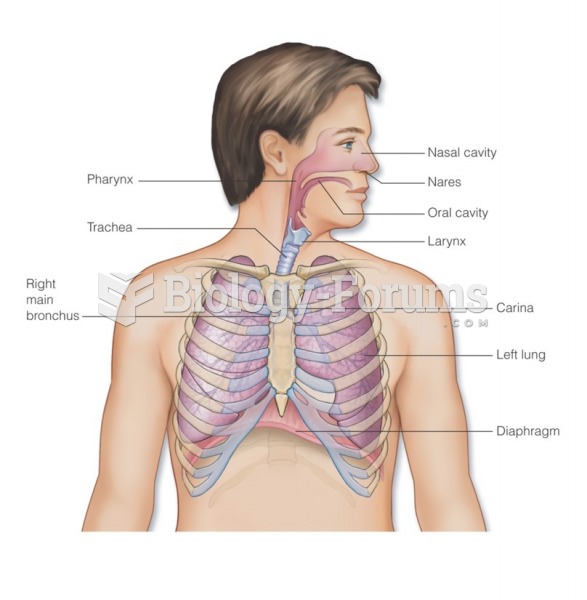
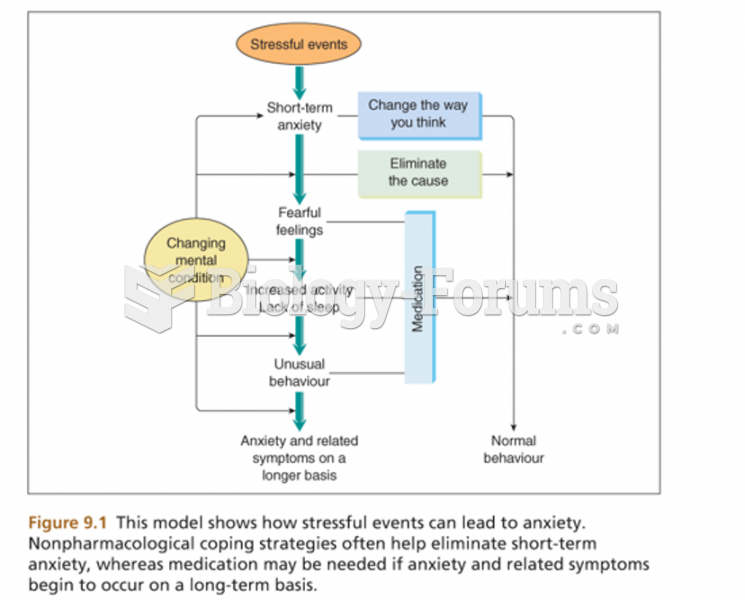
|
|
|
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
Asthma cases in Americans are about 75% higher today than they were in 1980.
Pregnant women usually experience a heightened sense of smell beginning late in the first trimester. Some experts call this the body's way of protecting a pregnant woman from foods that are unsafe for the fetus.
IgA antibodies protect body surfaces exposed to outside foreign substances. IgG antibodies are found in all body fluids. IgM antibodies are the first type of antibody made in response to an infection. IgE antibody levels are often high in people with allergies. IgD antibodies are found in tissues lining the abdomen and chest.
Asthma is the most common chronic childhood disease in the world. Most children who develop asthma have symptoms before they are 5 years old.