|
|
|
Signs of depression include feeling sad most of the time for 2 weeks or longer; loss of interest in things normally enjoyed; lack of energy; sleep and appetite disturbances; weight changes; feelings of hopelessness, helplessness, or worthlessness; an inability to make decisions; and thoughts of death and suicide.
Elderly adults are at greatest risk of stroke and myocardial infarction and have the most to gain from prophylaxis. Patients ages 60 to 80 years with blood pressures above 160/90 mm Hg should benefit from antihypertensive treatment.
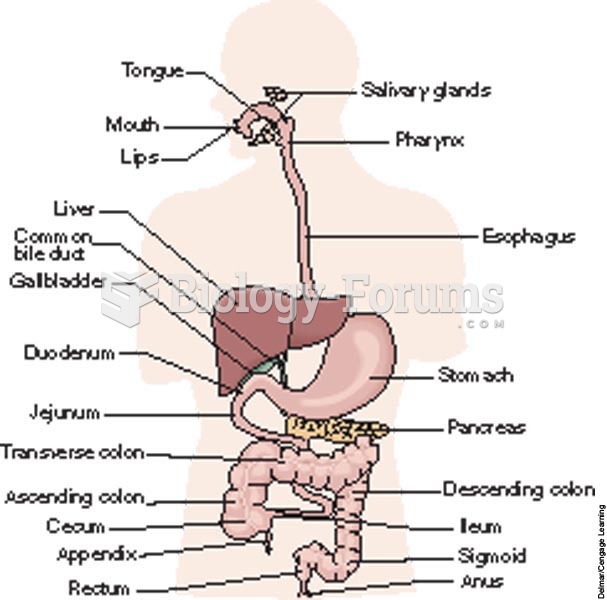
The top five reasons that children stay home from school are as follows: colds, stomach flu (gastroenteritis), ear infection (otitis media), pink eye (conjunctivitis), and sore throat.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
Your skin wrinkles if you stay in the bathtub a long time because the outermost layer of skin (which consists of dead keratin) swells when it absorbs water. It is tightly attached to the skin below it, so it compensates for the increased area by wrinkling. This happens to the hands and feet because they have the thickest layer of dead keratin cells.