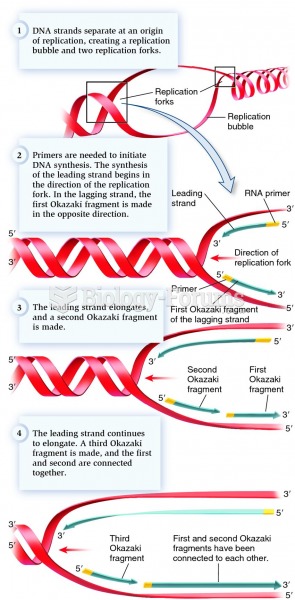
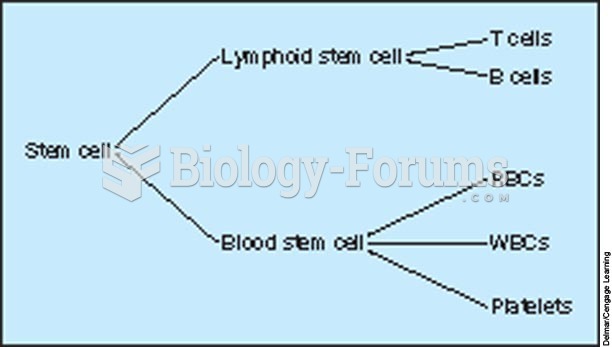
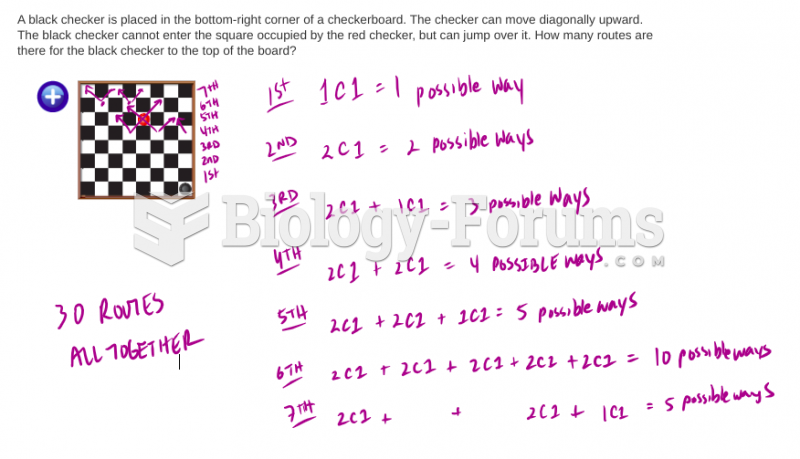
|
|
|
For high blood pressure (hypertension), a new class of drug, called a vasopeptidase blocker (inhibitor), has been developed. It decreases blood pressure by simultaneously dilating the peripheral arteries and increasing the body's loss of salt.
Acute bronchitis is an inflammation of the breathing tubes (bronchi), which causes increased mucus production and other changes. It is usually caused by bacteria or viruses, can be serious in people who have pulmonary or cardiac diseases, and can lead to pneumonia.
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Your skin wrinkles if you stay in the bathtub a long time because the outermost layer of skin (which consists of dead keratin) swells when it absorbs water. It is tightly attached to the skin below it, so it compensates for the increased area by wrinkling. This happens to the hands and feet because they have the thickest layer of dead keratin cells.
Medications that are definitely not safe to take when breastfeeding include radioactive drugs, antimetabolites, some cancer (chemotherapy) agents, bromocriptine, ergotamine, methotrexate, and cyclosporine.