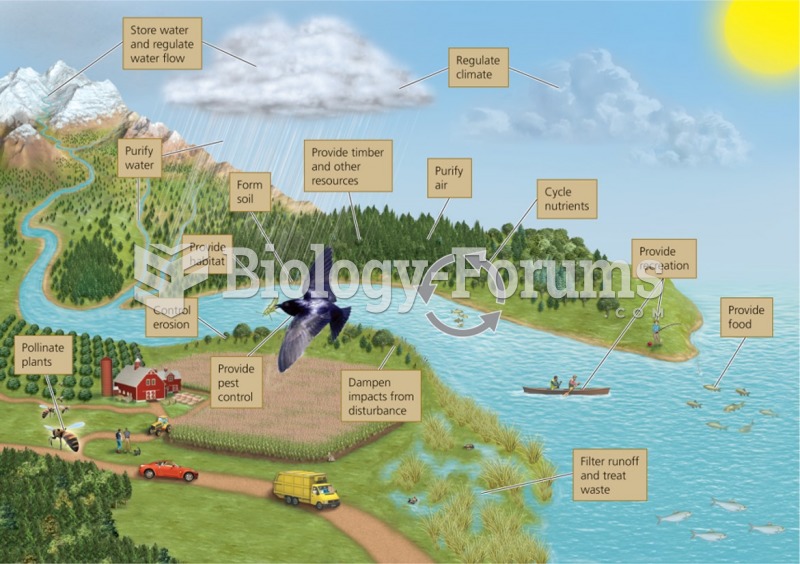
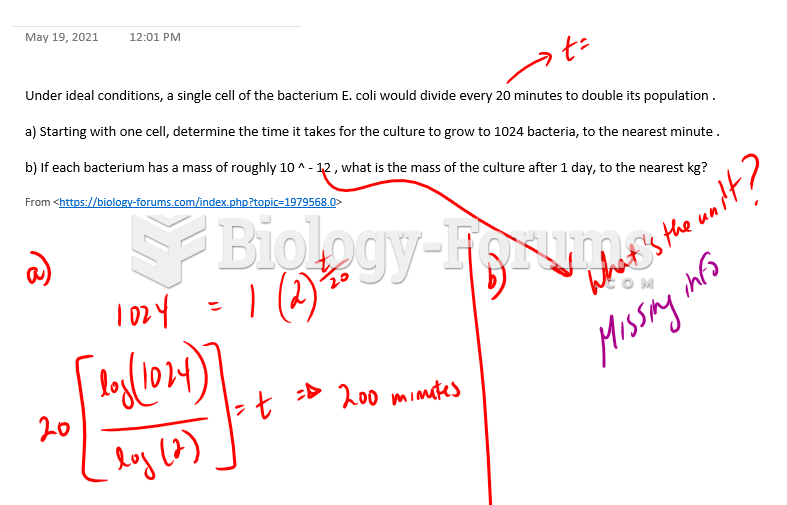
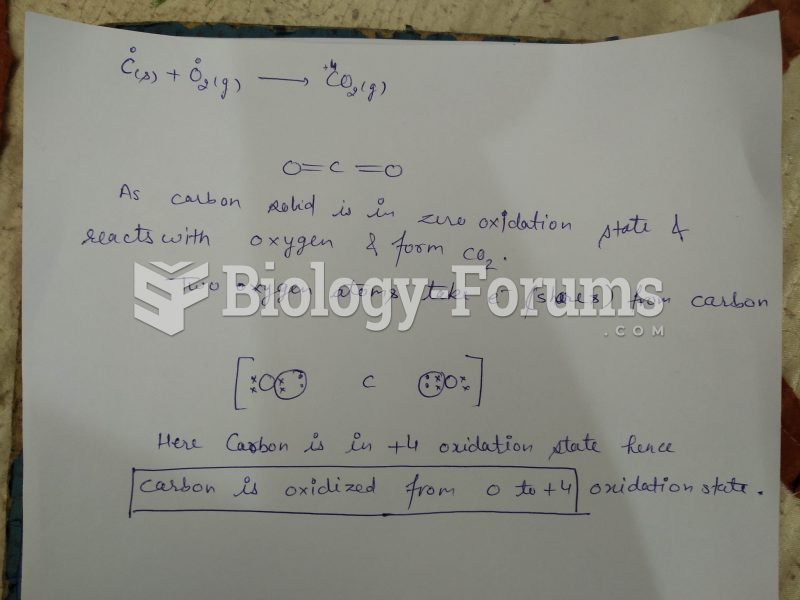
|
|
|
The modern decimal position system was the invention of the Hindus (around 800 AD), involving the placing of numerals to indicate their value (units, tens, hundreds, and so on).
It is important to read food labels and choose foods with low cholesterol and saturated trans fat. You should limit saturated fat to no higher than 6% of daily calories.
In the United States, congenital cytomegalovirus causes one child to become disabled almost every hour. CMV is the leading preventable viral cause of development disability in newborns. These disabilities include hearing or vision loss, and cerebral palsy.
Eating food that has been cooked with poppy seeds may cause you to fail a drug screening test, because the seeds contain enough opiate alkaloids to register as a positive.
Most strokes are caused when blood clots move to a blood vessel in the brain and block blood flow to that area. Thrombolytic therapy can be used to dissolve the clot quickly. If given within 3 hours of the first stroke symptoms, this therapy can help limit stroke damage and disability.