|
|
|
About one in five American adults and teenagers have had a genital herpes infection—and most of them don't know it. People with genital herpes have at least twice the risk of becoming infected with HIV if exposed to it than those people who do not have genital herpes.
The shortest mature adult human of whom there is independent evidence was Gul Mohammed in India. In 1990, he was measured in New Delhi and stood 22.5 inches tall.
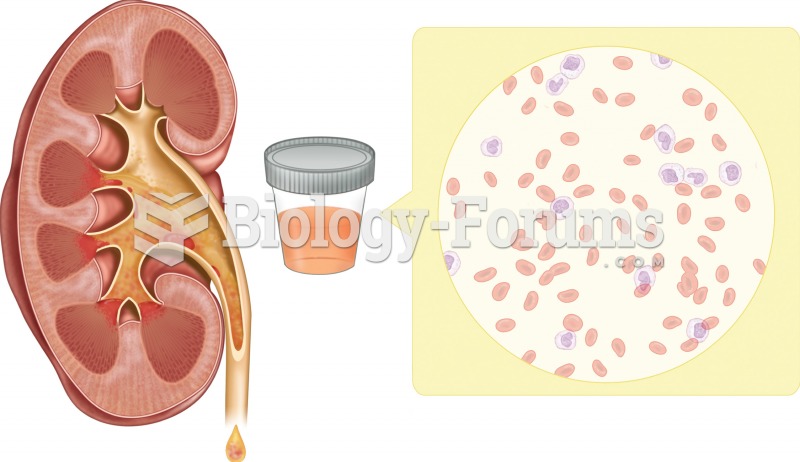
Hip fractures are the most serious consequences of osteoporosis. The incidence of hip fractures increases with each decade among patients in their 60s to patients in their 90s for both women and men of all populations. Men and women older than 80 years of age show the highest incidence of hip fractures.
The top 10 most important tips that will help you grow old gracefully include (1) quit smoking, (2) keep your weight down, (3) take supplements, (4) skip a meal each day or fast 1 day per week, (5) get a pet, (6) get medical help for chronic pain, (7) walk regularly, (8) reduce arguments, (9) put live plants in your living space, and (10) do some weight training.
Children of people with alcoholism are more inclined to drink alcohol or use hard drugs. In fact, they are 400 times more likely to use hard drugs than those who do not have a family history of alcohol addiction.