|
|
|
There are more sensory neurons in the tongue than in any other part of the body.
In 1864, the first barbiturate (barbituric acid) was synthesized.
Asthma is the most common chronic childhood disease in the world. Most children who develop asthma have symptoms before they are 5 years old.
According to the American College of Allergy, Asthma & Immunology, more than 50 million Americans have some kind of food allergy. Food allergies affect between 4 and 6% of children, and 4% of adults, according to the CDC. The most common food allergies include shellfish, peanuts, walnuts, fish, eggs, milk, and soy.
About 80% of major fungal systemic infections are due to Candida albicans. Another form, Candida peritonitis, occurs most often in postoperative patients. A rare disease, Candida meningitis, may follow leukemia, kidney transplant, other immunosuppressed factors, or when suffering from Candida septicemia.
 Large size can provide a refuge from predators. While young African elephants may be vulnerable to p
Large size can provide a refuge from predators. While young African elephants may be vulnerable to p
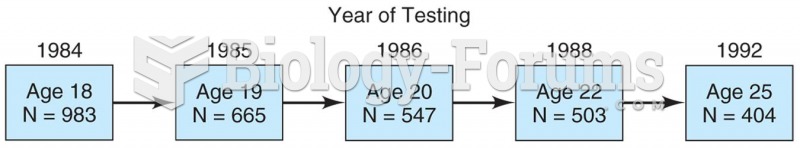 Model of a longitudinal study in which 983 students were surveyed in 1984 and then again in 1985, 19
Model of a longitudinal study in which 983 students were surveyed in 1984 and then again in 1985, 19