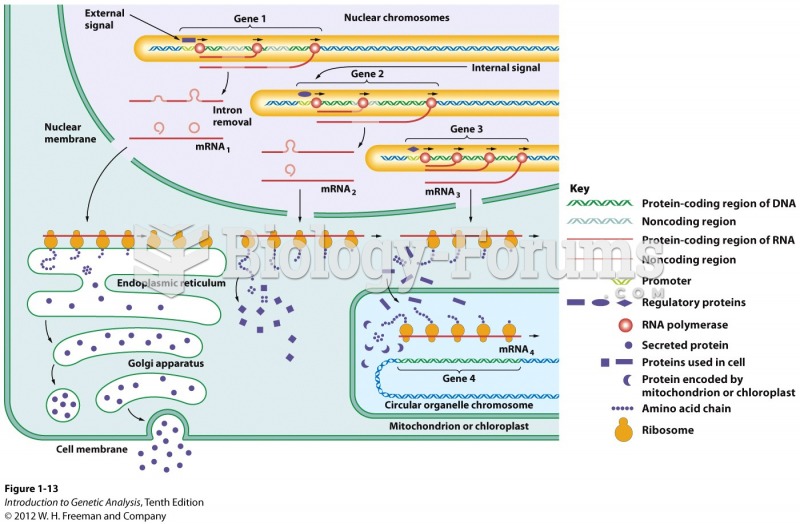
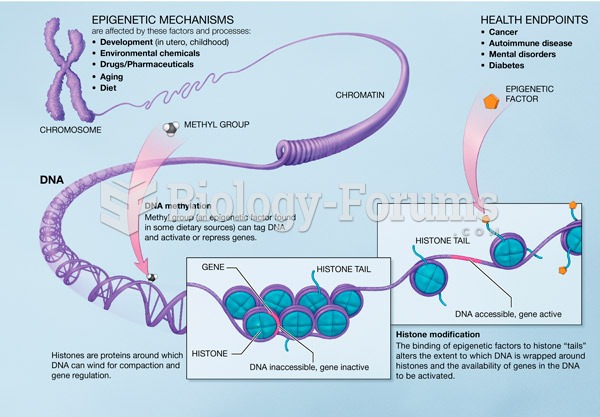
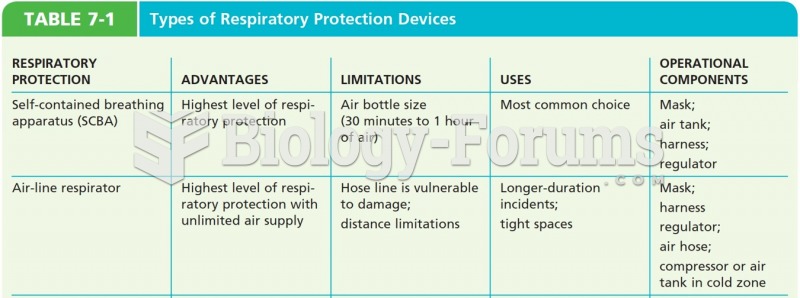
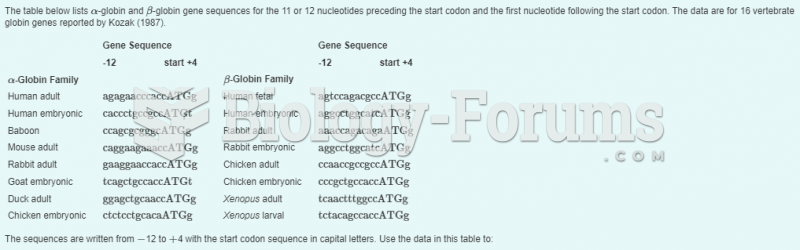
|
|
|
Once thought to have neurofibromatosis, Joseph Merrick (also known as "the elephant man") is now, in retrospect, thought by clinical experts to have had Proteus syndrome. This endocrine disease causes continued and abnormal growth of the bones, muscles, skin, and so on and can become completely debilitating with severe deformities occurring anywhere on the body.
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.
Approximately one in three babies in the United States is now delivered by cesarean section. The number of cesarean sections in the United States has risen 46% since 1996.
Walt Disney helped combat malaria by making an animated film in 1943 called The Winged Scourge. This short film starred the seven dwarfs and taught children that mosquitos transmit malaria, which is a very bad disease. It advocated the killing of mosquitos to stop the disease.
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.