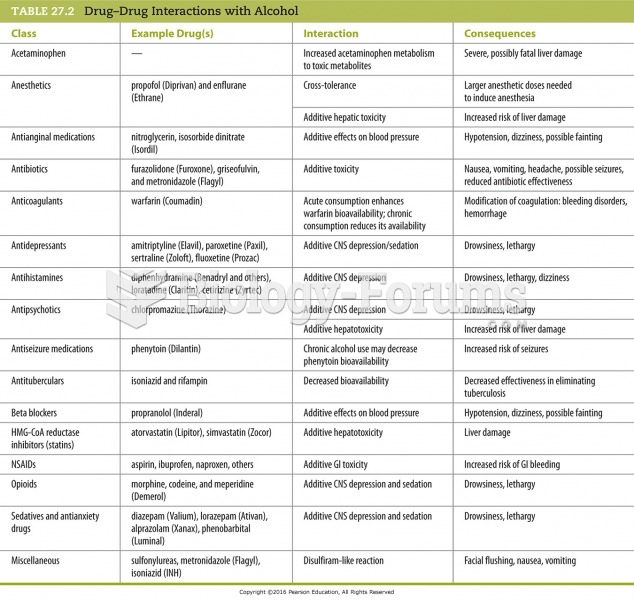
|
|
|
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.
Many supplement containers do not even contain what their labels say. There are many documented reports of products containing much less, or more, that what is listed on their labels. They may also contain undisclosed prescription drugs and even contaminants.
Cutaneous mucormycosis is a rare fungal infection that has been fatal in at least 29% of cases, and in as many as 83% of cases, depending on the patient's health prior to infection. It has occurred often after natural disasters such as tornados, and early treatment is essential.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.