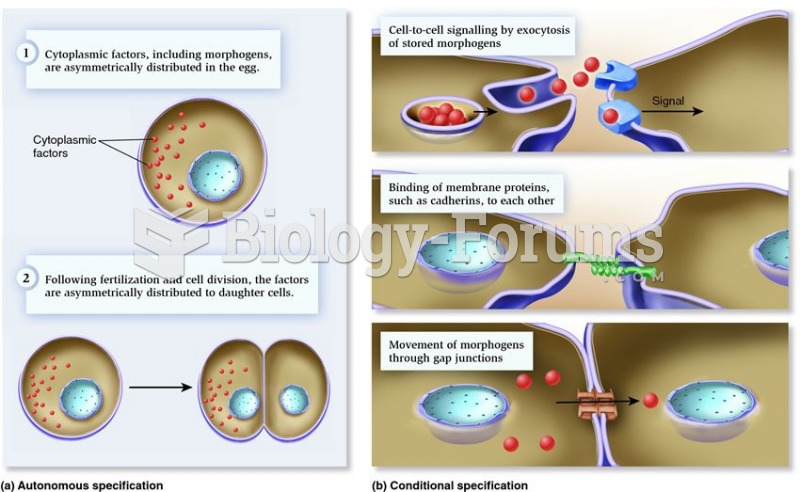
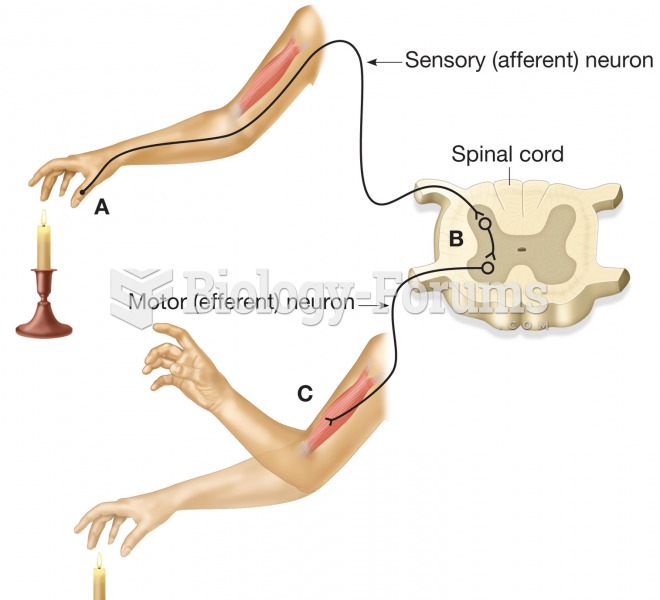
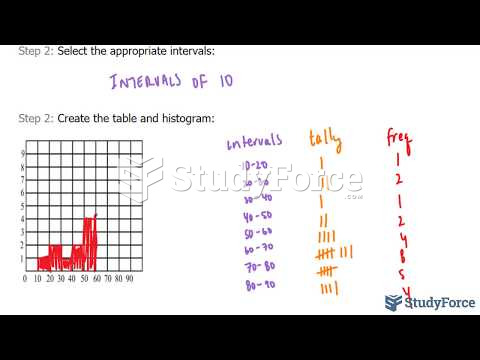
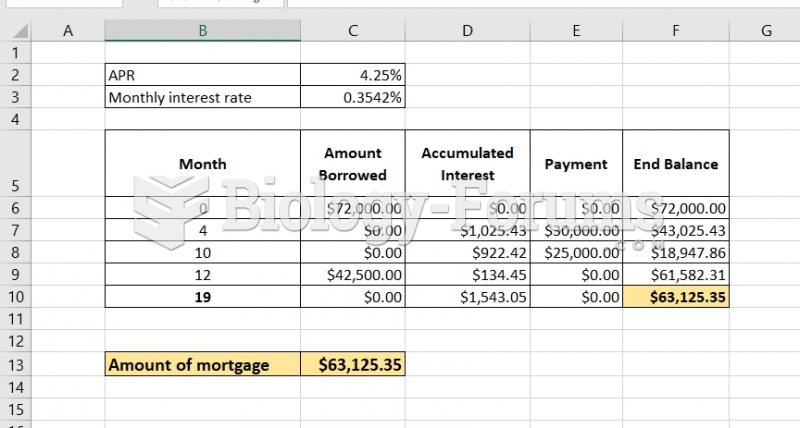
|
|
|
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
The word drug comes from the Dutch word droog (meaning "dry"). For centuries, most drugs came from dried plants, hence the name.
Many medications that are used to treat infertility are injected subcutaneously. This is easy to do using the anterior abdomen as the site of injection but avoiding the area directly around the belly button.
Fungal nail infections account for up to 30% of all skin infections. They affect 5% of the general population—mostly people over the age of 70.
Drug abusers experience the following scenario: The pleasure given by their drug (or drugs) of choice is so strong that it is difficult to eradicate even after years of staying away from the substances involved. Certain triggers may cause a drug abuser to relapse. Research shows that long-term drug abuse results in significant changes in brain function that persist long after an individual stops using drugs. It is most important to realize that the same is true of not just illegal substances but alcohol and tobacco as well.