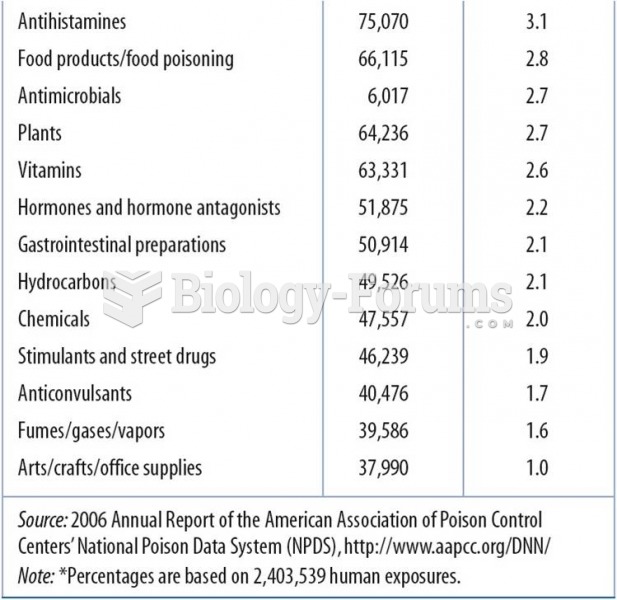
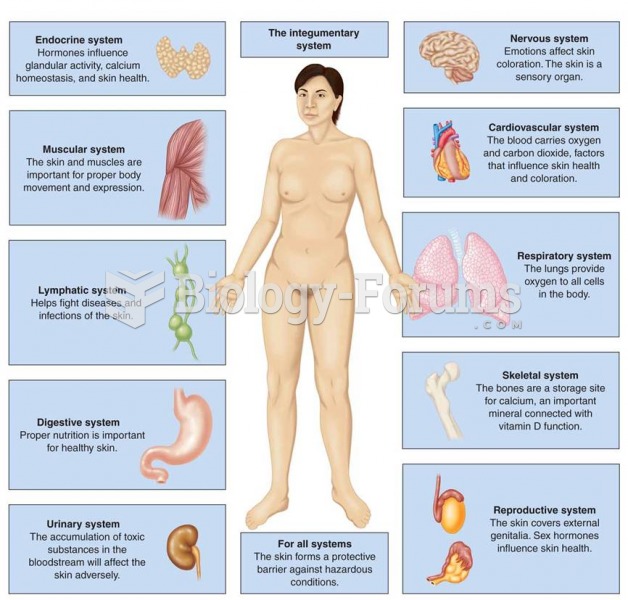
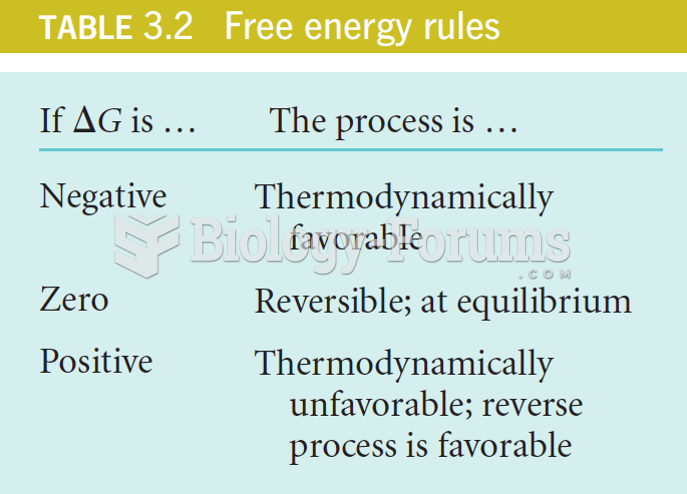
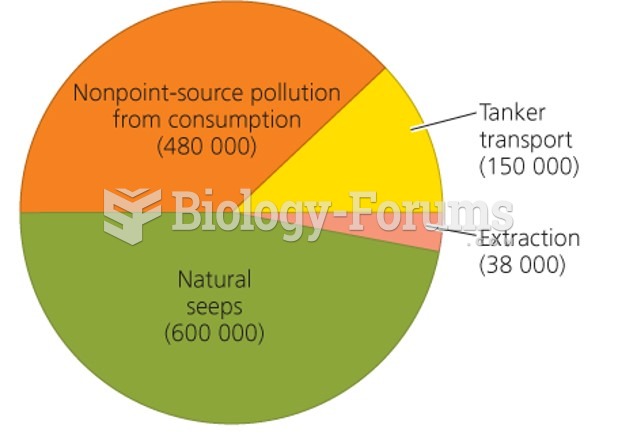
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
The most common childhood diseases include croup, chickenpox, ear infections, flu, pneumonia, ringworm, respiratory syncytial virus, scabies, head lice, and asthma.
Did you know?
The FDA recognizes 118 routes of administration.
Did you know?
Persons who overdose with cardiac glycosides have a better chance of overall survival if they can survive the first 24 hours after the overdose.
Did you know?
Multiple sclerosis is a condition wherein the body's nervous system is weakened by an autoimmune reaction that attacks the myelin sheaths of neurons.
Did you know?
Human stomach acid is strong enough to dissolve small pieces of metal such as razor blades or staples.