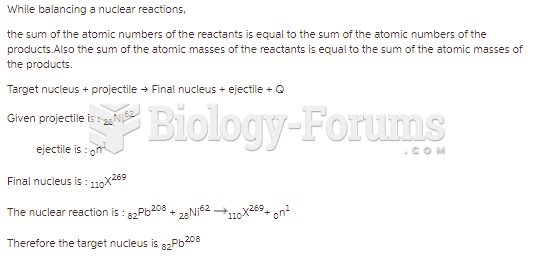
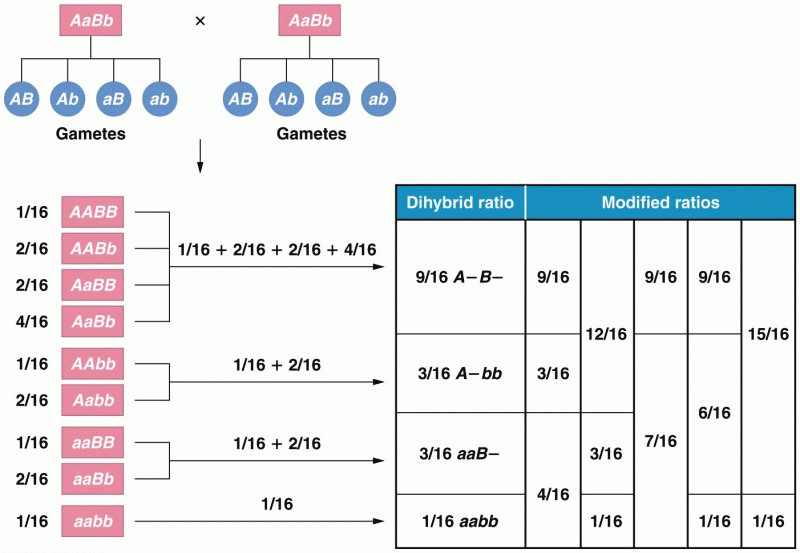
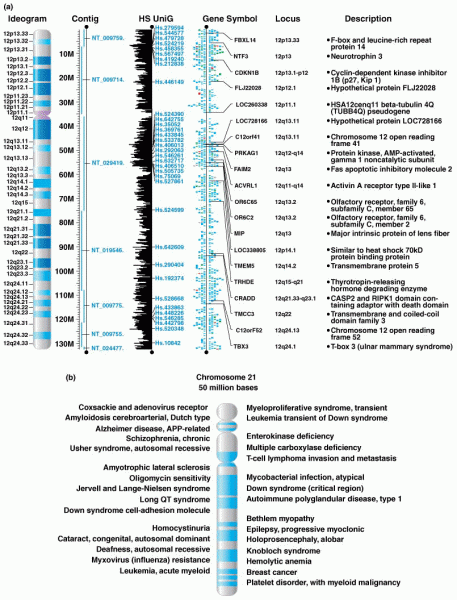
Answer to Question 1
C
Answer to Question 2
Network topology refers to the shape of a network. The four common network topologies are star, ring, bus, and mesh.
A star network is configured in the shape of a star. That is, all nodes or workstations are connected to a central hub, or concentrator, through which all messages pass. The workstations represent the points of the star. Star topologies are easy to lay out and modify. However, they are also the most costly because they require the largest amount of cabling. Although it is easy to diagnose problems at individual workstations, star networks are susceptible to a single point of failure at the hub that would result in all workstations losing network access.
A ring network is configured in the shape of a closed loop or circle with each node connecting to the next node. In ring networks, messages move in one direction around the circle. As a message moves around the circle, each workstation examines it to see whether the message is for that workstation. If not, the message is regenerated and passed on to the next node. This regeneration process enables ring networks to cover much larger distances than star or bus networks can. Relatively little cabling is required, but a failure of any node on the ring network can cause complete network failure. Self-healing ring networks avoid this by having two rings with data flowing in different directions; thus, the failure of a single node does not cause the network to fail. In either case, it is difficult to modify and reconfigure a ring network. Ring networks normally use some form of token-passing media access control method to regulate network traffic.
A bus network is in the shape of an open-ended line; as a result, it is the easiest network to extend and has the simplest wiring layout. This topology enables all network nodes to receive the same message through the network cable at the same time. However, it is difficult to diagnose and isolate network faults. Bus networks use variants of CSMA for media access control.
A mesh network consists of computers and other devices that are either fully or partially connected to each other. In a full mesh design, every computer and device is connected to every other computer and device. In a partial mesh design, many but not all computers and devices are connected. Like a ring network, mesh networks provide relatively short routes from one node to another. Mesh networks also provide many possible routes through the network-a design that prevents one circuit or computer from becoming overloaded when traffic is heavy. Given these benefits, most WANs, including the Internet, use a partial mesh design.