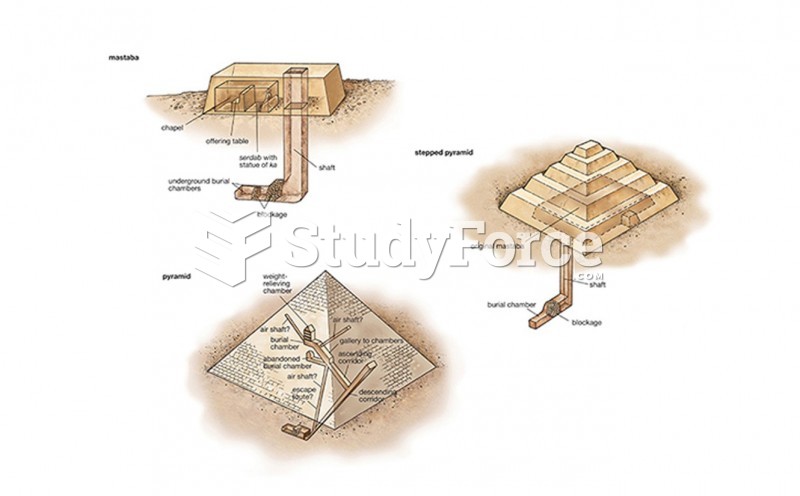
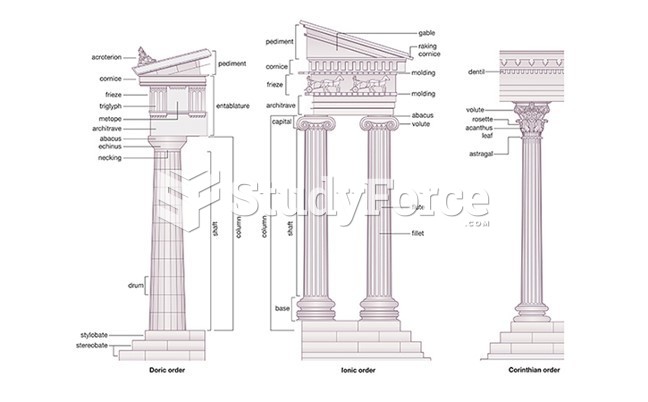
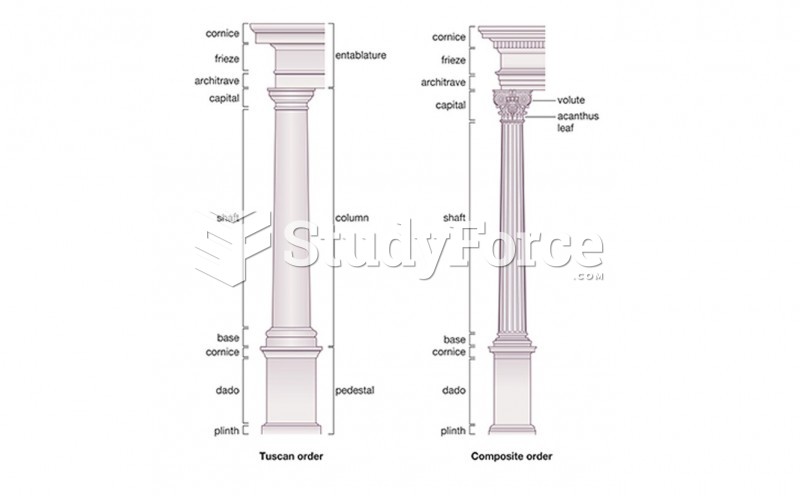
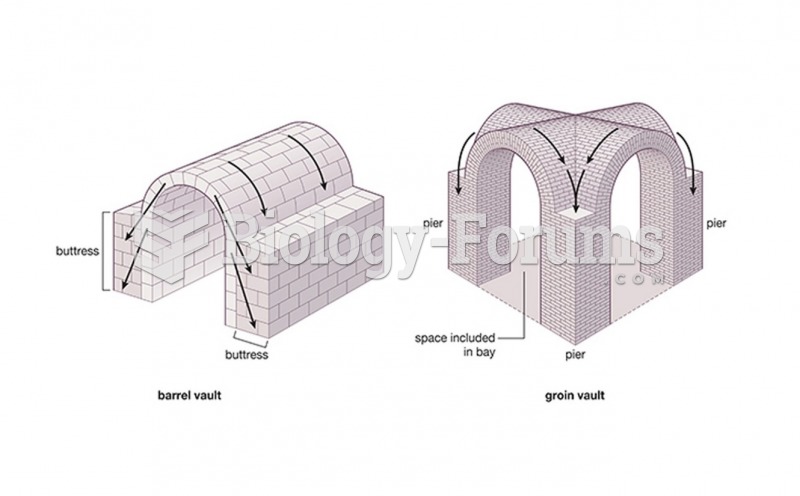
|
|
|
Multiple experimental evidences have confirmed that at the molecular level, cancer is caused by lesions in cellular DNA.
Hip fractures are the most serious consequences of osteoporosis. The incidence of hip fractures increases with each decade among patients in their 60s to patients in their 90s for both women and men of all populations. Men and women older than 80 years of age show the highest incidence of hip fractures.
Urine turns bright yellow if larger than normal amounts of certain substances are consumed; one of these substances is asparagus.
About 3.2 billion people, nearly half the world population, are at risk for malaria. In 2015, there are about 214 million malaria cases and an estimated 438,000 malaria deaths.
There are more bacteria in your mouth than there are people in the world.