|
|
|
Though Candida and Aspergillus species are the most common fungal pathogens causing invasive fungal disease in the immunocompromised, infections due to previously uncommon hyaline and dematiaceous filamentous fungi are occurring more often today. Rare fungal infections, once accurately diagnosed, may require surgical debridement, immunotherapy, and newer antifungals used singly or in combination with older antifungals, on a case-by-case basis.
Inotropic therapy does not have a role in the treatment of most heart failure patients. These drugs can make patients feel and function better but usually do not lengthen the predicted length of their lives.
In women, pharmacodynamic differences include increased sensitivity to (and increased effectiveness of) beta-blockers, opioids, selective serotonin reuptake inhibitors, and typical antipsychotics.
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.
The Romans did not use numerals to indicate fractions but instead used words to indicate parts of a whole.
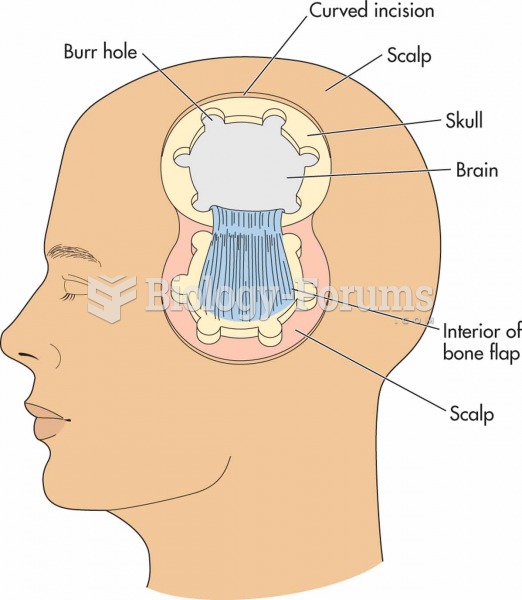 In a craniotomy, a portion of the skull and overlying scalp is pulled back to allow access to the br
In a craniotomy, a portion of the skull and overlying scalp is pulled back to allow access to the br
 French and U.S. presidential elections in 2012 illustrate the durability of political culture and ho
French and U.S. presidential elections in 2012 illustrate the durability of political culture and ho



