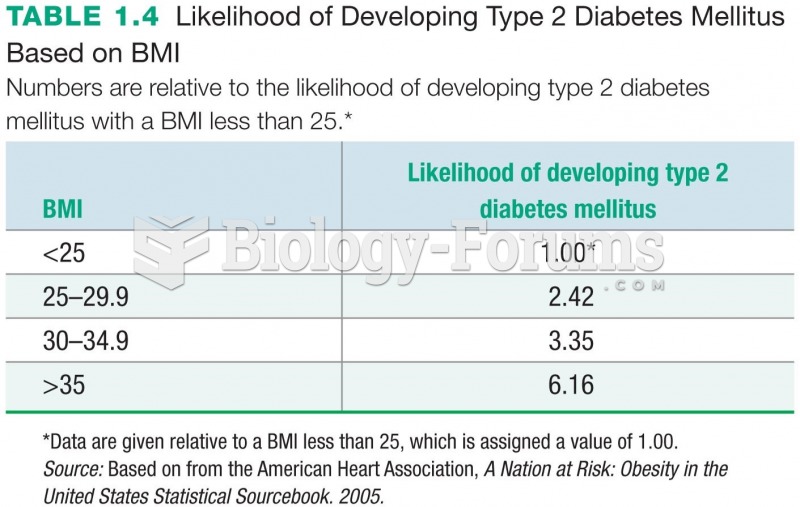
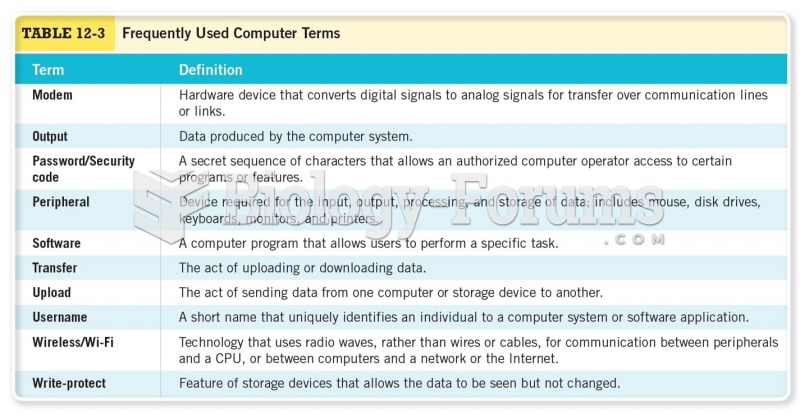
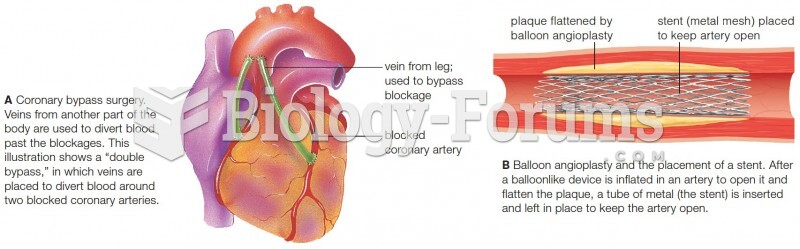
|
|
|
Asthma occurs in one in 11 children and in one in 12 adults. African Americans and Latinos have a higher risk for developing asthma than other groups.
Blood is approximately twice as thick as water because of the cells and other components found in it.
Aspirin may benefit 11 different cancers, including those of the colon, pancreas, lungs, prostate, breasts, and leukemia.
Coca-Cola originally used coca leaves and caffeine from the African kola nut. It was advertised as a therapeutic agent and "pickerupper." Eventually, its formulation was changed, and the coca leaves were removed because of the effects of regulation on cocaine-related products.
Only 12 hours after an egg cell is fertilized by a sperm cell, the egg cell starts to divide. As it continues to divide, it moves along the fallopian tube toward the uterus at about 1 inch per day.