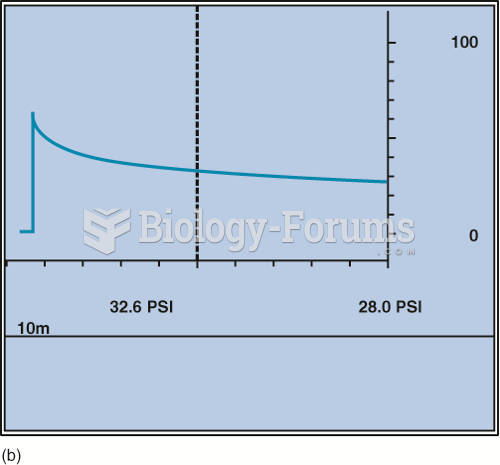
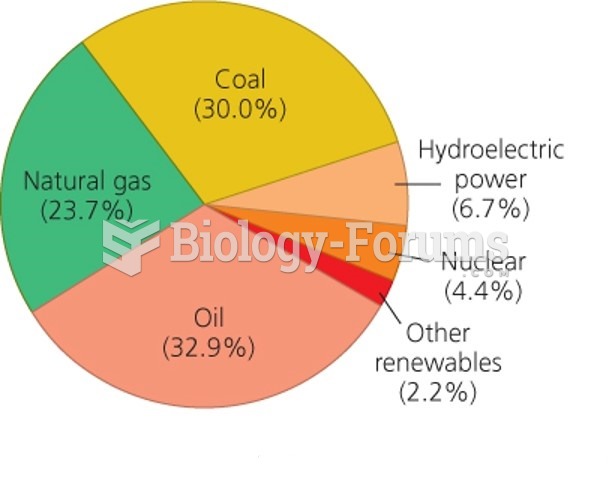
|
|
|
Signs of depression include feeling sad most of the time for 2 weeks or longer; loss of interest in things normally enjoyed; lack of energy; sleep and appetite disturbances; weight changes; feelings of hopelessness, helplessness, or worthlessness; an inability to make decisions; and thoughts of death and suicide.
When blood is exposed to air, it clots. Heparin allows the blood to come in direct contact with air without clotting.
Although puberty usually occurs in the early teenage years, the world's youngest parents were two Chinese children who had their first baby when they were 8 and 9 years of age.
In the United States, congenital cytomegalovirus causes one child to become disabled almost every hour. CMV is the leading preventable viral cause of development disability in newborns. These disabilities include hearing or vision loss, and cerebral palsy.
Once thought to have neurofibromatosis, Joseph Merrick (also known as "the elephant man") is now, in retrospect, thought by clinical experts to have had Proteus syndrome. This endocrine disease causes continued and abnormal growth of the bones, muscles, skin, and so on and can become completely debilitating with severe deformities occurring anywhere on the body.