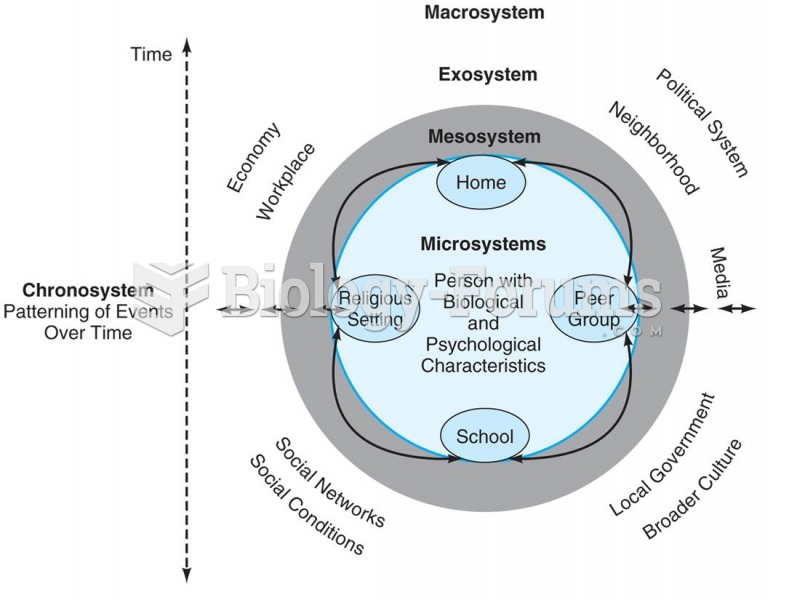
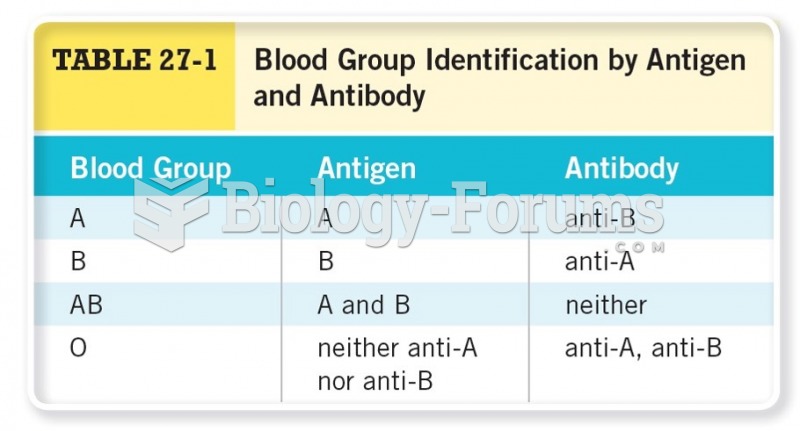
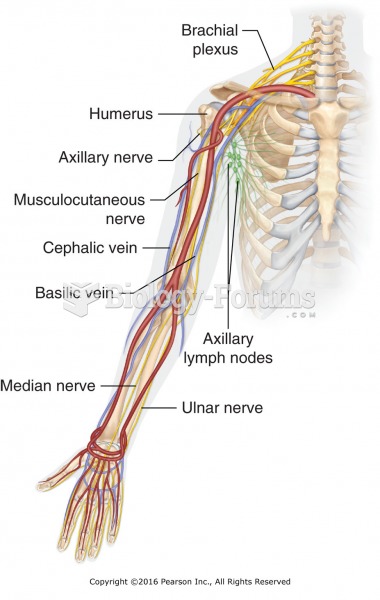
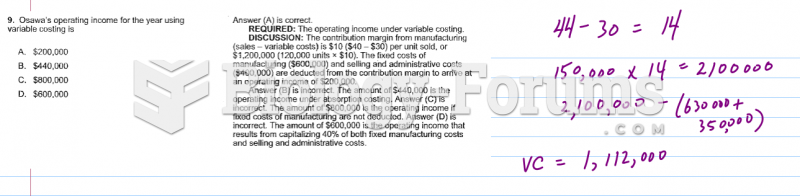
|
|
|
Eating food that has been cooked with poppy seeds may cause you to fail a drug screening test, because the seeds contain enough opiate alkaloids to register as a positive.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.
You should not take more than 1,000 mg of vitamin E per day. Doses above this amount increase the risk of bleeding problems that can lead to a stroke.
Most strokes are caused when blood clots move to a blood vessel in the brain and block blood flow to that area. Thrombolytic therapy can be used to dissolve the clot quickly. If given within 3 hours of the first stroke symptoms, this therapy can help limit stroke damage and disability.
Despite claims by manufacturers, the supplement known as Ginkgo biloba was shown in a study of more than 3,000 participants to be ineffective in reducing development of dementia and Alzheimer’s disease in older people.