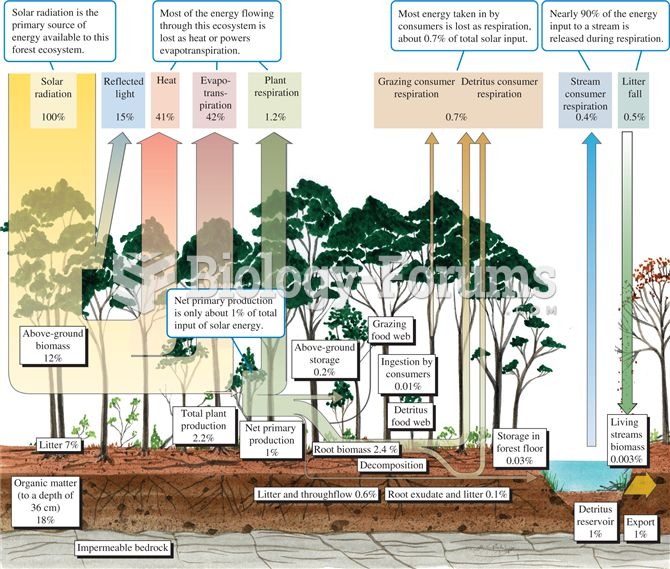
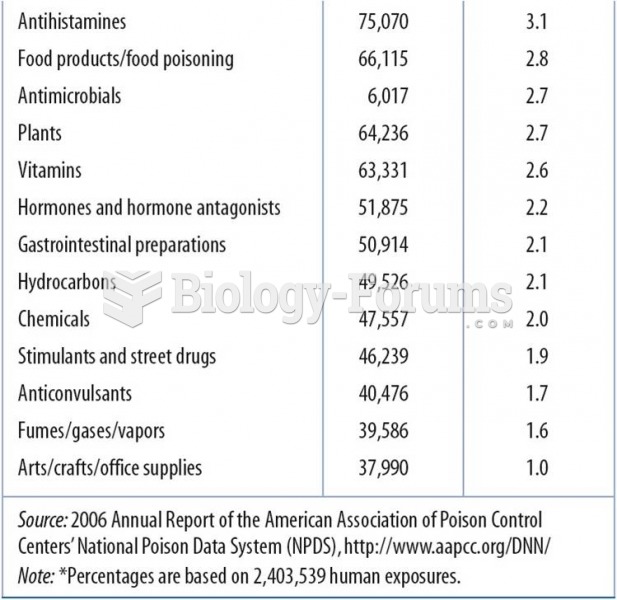
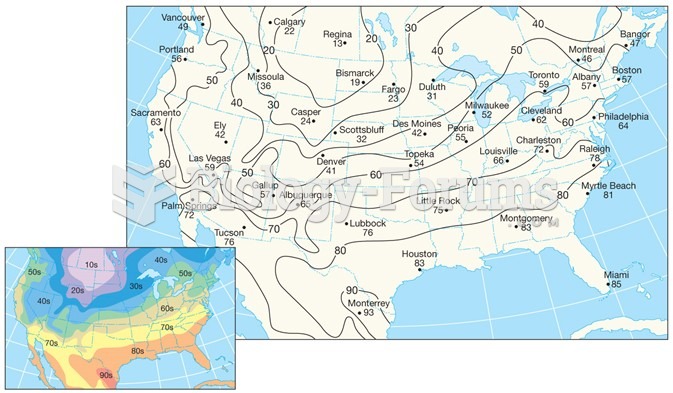
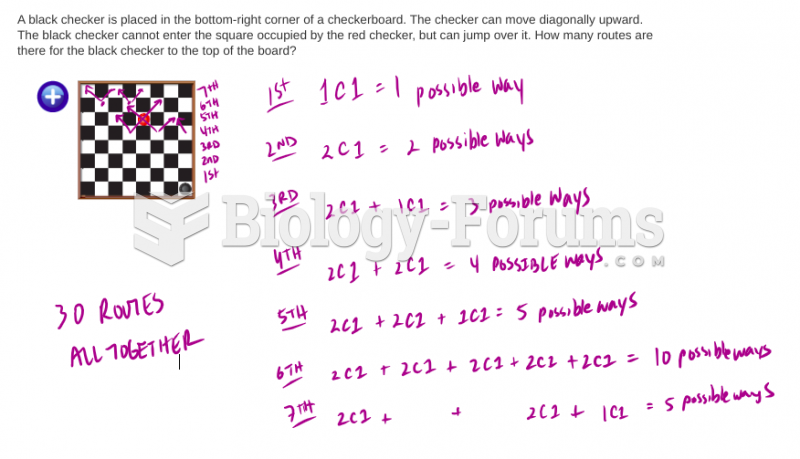
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
There are more bacteria in your mouth than there are people in the world.
Did you know?
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.
Did you know?
The word drug comes from the Dutch word droog (meaning "dry"). For centuries, most drugs came from dried plants, hence the name.
Did you know?
The first oral chemotherapy drug for colon cancer was approved by FDA in 2001.
Did you know?
More than 150,000 Americans killed by cardiovascular disease are younger than the age of 65 years.