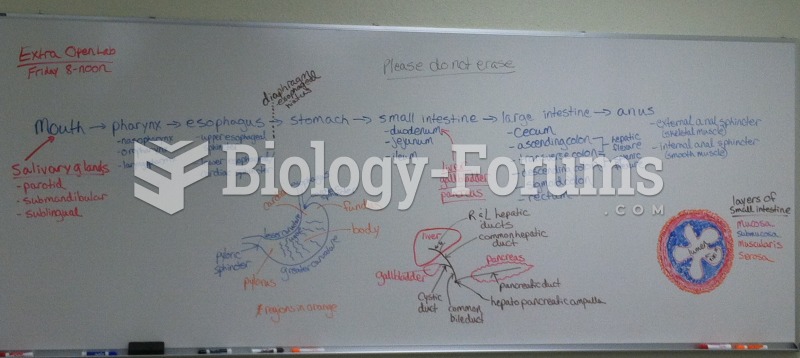
|
|
|
For high blood pressure (hypertension), a new class of drug, called a vasopeptidase blocker (inhibitor), has been developed. It decreases blood pressure by simultaneously dilating the peripheral arteries and increasing the body's loss of salt.
Vital signs (blood pressure, temperature, pulse rate, respiration rate) should be taken before any drug administration. Patients should be informed not to use tobacco or caffeine at least 30 minutes before their appointment.
The Centers for Disease Control and Prevention has released reports detailing the deaths of infants (younger than 1 year of age) who died after being given cold and cough medications. This underscores the importance of educating parents that children younger than 2 years of age should never be given over-the-counter cold and cough medications without consulting their physicians.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
There are more sensory neurons in the tongue than in any other part of the body.