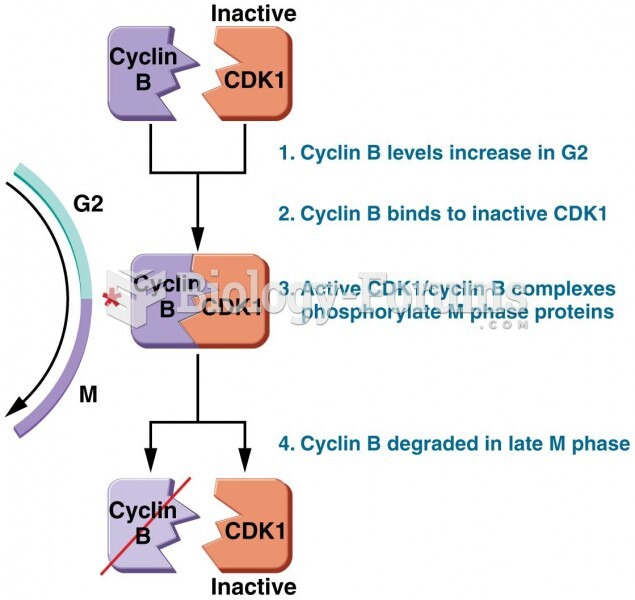
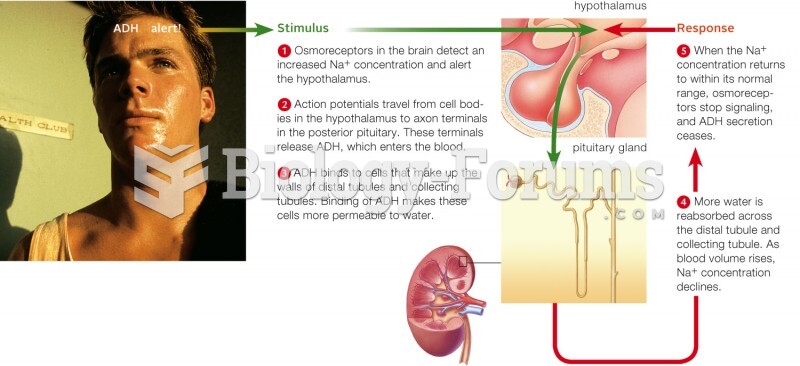
|
|
|
Coca-Cola originally used coca leaves and caffeine from the African kola nut. It was advertised as a therapeutic agent and "pickerupper." Eventually, its formulation was changed, and the coca leaves were removed because of the effects of regulation on cocaine-related products.
Patients who have undergone chemotherapy for the treatment of cancer often complain of a lack of mental focus; memory loss; and a general diminution in abilities such as multitasking, attention span, and general mental agility.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
Signs of depression include feeling sad most of the time for 2 weeks or longer; loss of interest in things normally enjoyed; lack of energy; sleep and appetite disturbances; weight changes; feelings of hopelessness, helplessness, or worthlessness; an inability to make decisions; and thoughts of death and suicide.
Most women experience menopause in their 50s. However, in 1994, an Italian woman gave birth to a baby boy when she was 61 years old.