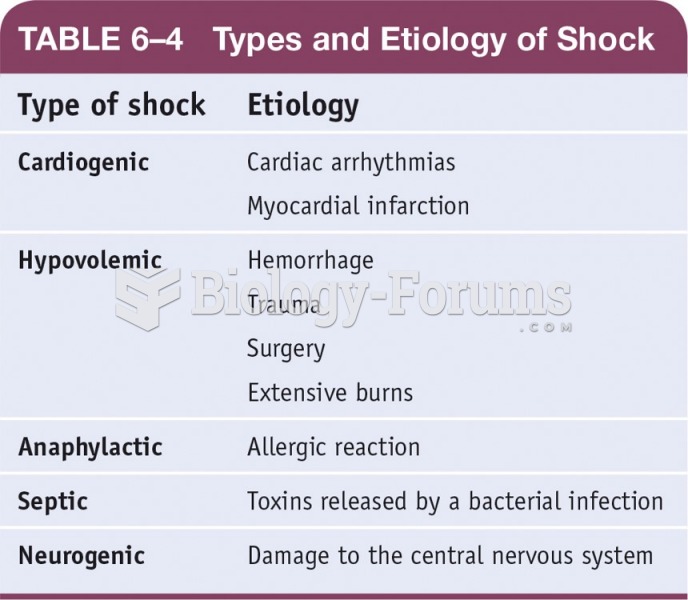
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
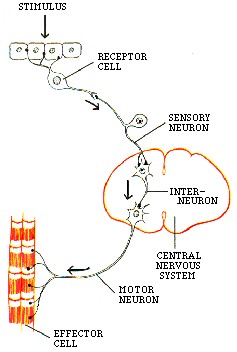
If all the neurons in the human body were lined up, they would stretch more than 600 miles.
Did you know?
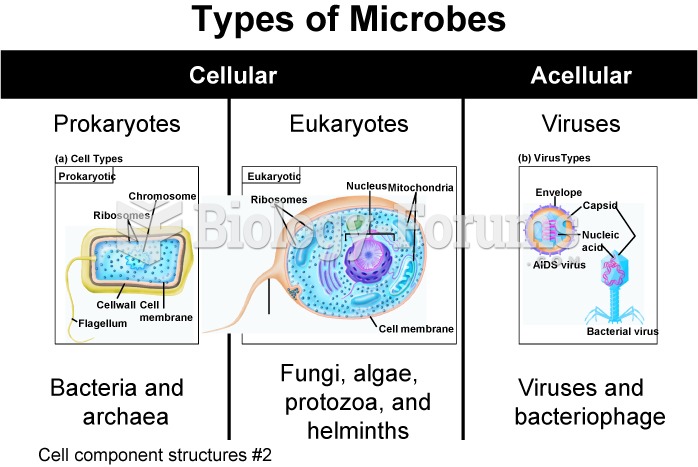
The average office desk has 400 times more bacteria on it than a toilet.
Did you know?
Although not all of the following muscle groups are commonly used, intramuscular injections may be given into the abdominals, biceps, calves, deltoids, gluteals, laterals, pectorals, quadriceps, trapezoids, and triceps.
Did you know?
Asthma cases in Americans are about 75% higher today than they were in 1980.
Did you know?
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.