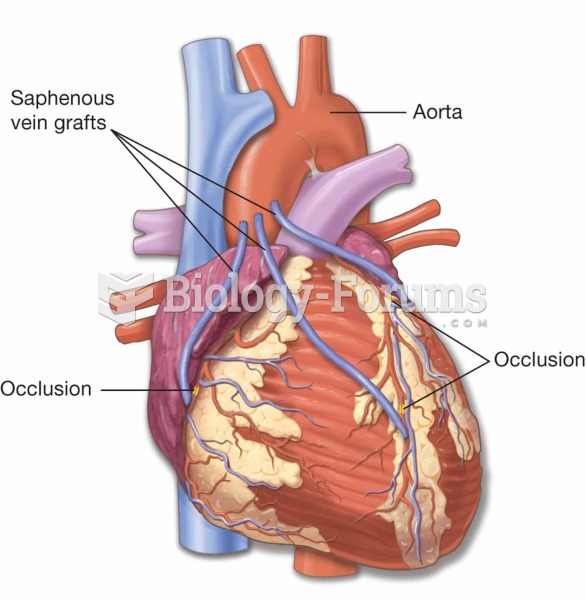
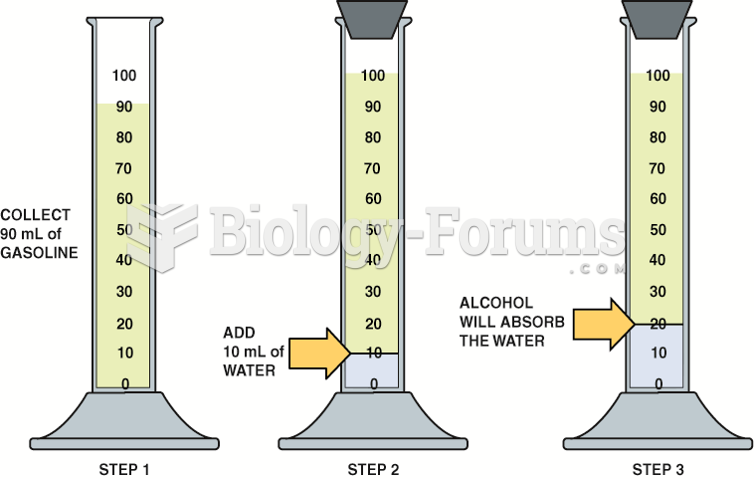
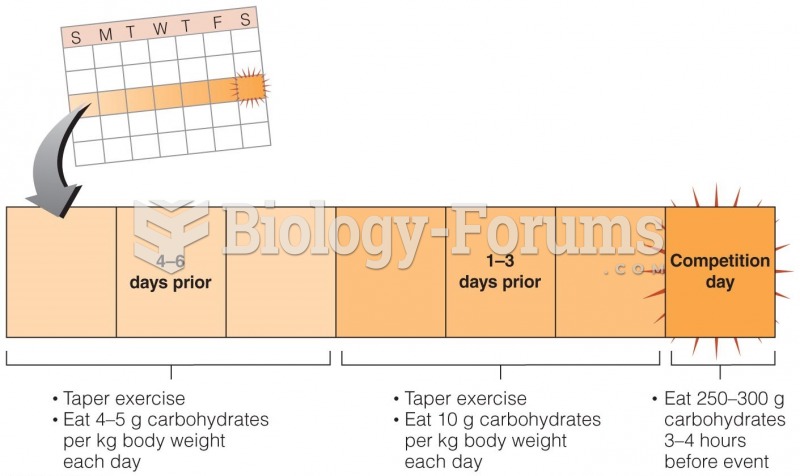
|
|
|
There are over 65,000 known species of protozoa. About 10,000 species are parasitic.
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
People about to have surgery must tell their health care providers about all supplements they take.
A strange skin disease referred to as Morgellons has occurred in the southern United States and in California. Symptoms include slowly healing sores, joint pain, persistent fatigue, and a sensation of things crawling through the skin. Another symptom is strange-looking, threadlike extrusions coming out of the skin.
Illness; diuretics; laxative abuse; hot weather; exercise; sweating; caffeine; alcoholic beverages; starvation diets; inadequate carbohydrate consumption; and diets high in protein, salt, or fiber can cause people to become dehydrated.