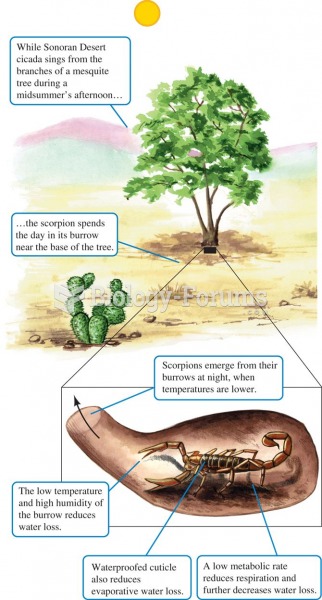
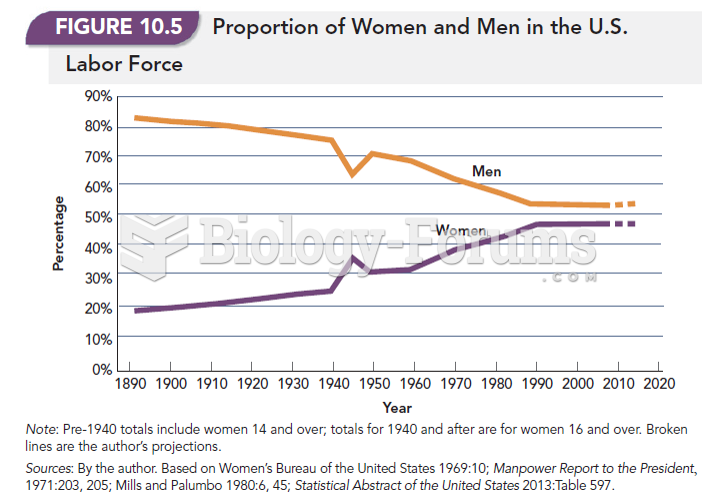
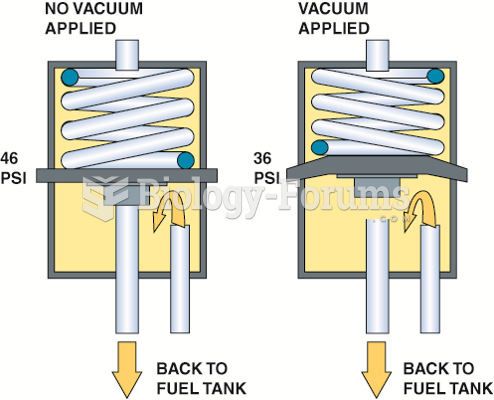
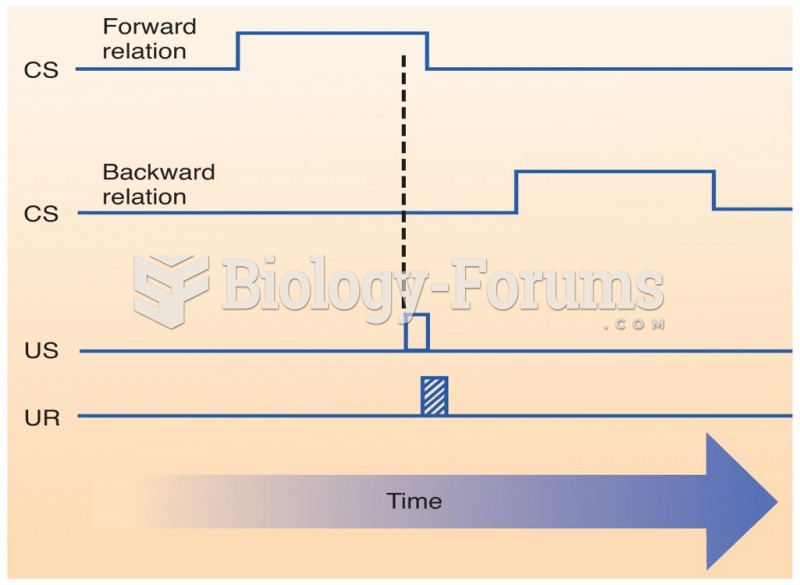
|
|
|
The cure for trichomoniasis is easy as long as the patient does not drink alcoholic beverages for 24 hours. Just a single dose of medication is needed to rid the body of the disease. However, without proper precautions, an individual may contract the disease repeatedly. In fact, most people develop trichomoniasis again within three months of their last treatment.
The term pharmacology is derived from the Greek words pharmakon("claim, medicine, poison, or remedy") and logos ("study").
Nearly 31 million adults in America have a total cholesterol level that is more than 240 mg per dL.
The oldest recorded age was 122. Madame Jeanne Calment was born in France in 1875 and died in 1997. She was a vegetarian and loved olive oil, port wine, and chocolate.
Although the Roman numeral for the number 4 has always been taught to have been "IV," according to historians, the ancient Romans probably used "IIII" most of the time. This is partially backed up by the fact that early grandfather clocks displayed IIII for the number 4 instead of IV. Early clockmakers apparently thought that the IIII balanced out the VIII (used for the number 8) on the clock face and that it just looked better.