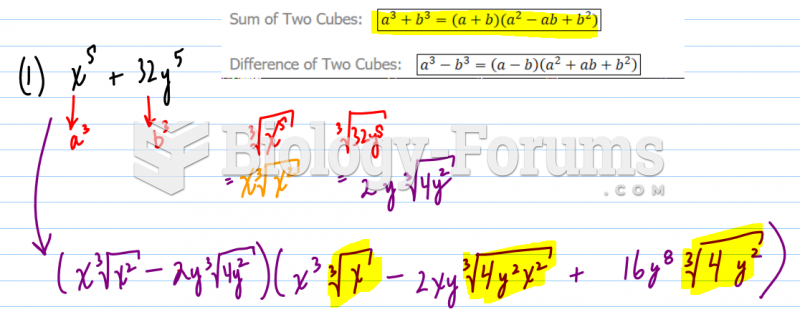
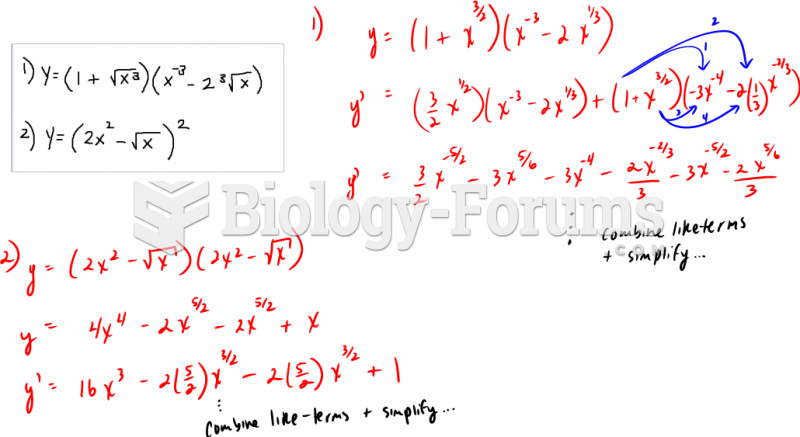
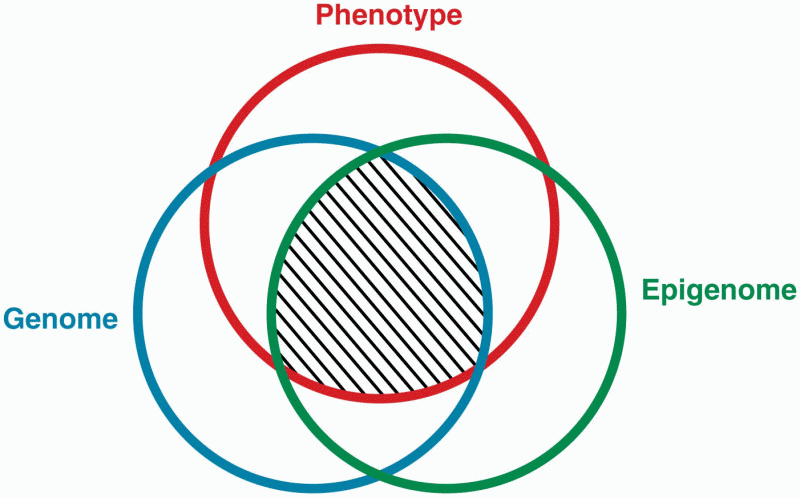
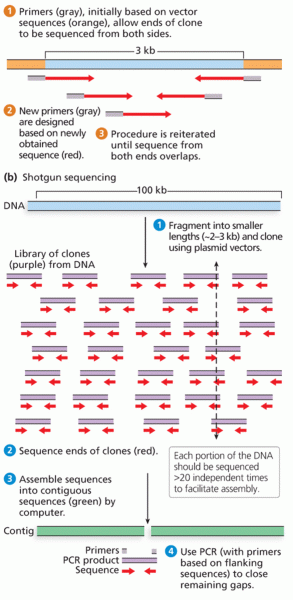
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
Did you know?
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.
Did you know?
More than 20 million Americans cite use of marijuana within the past 30 days, according to the National Survey on Drug Use and Health (NSDUH). More than 8 million admit to using it almost every day.
Did you know?
Eat fiber! A diet high in fiber can help lower cholesterol levels by as much as 10%.
Did you know?
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.