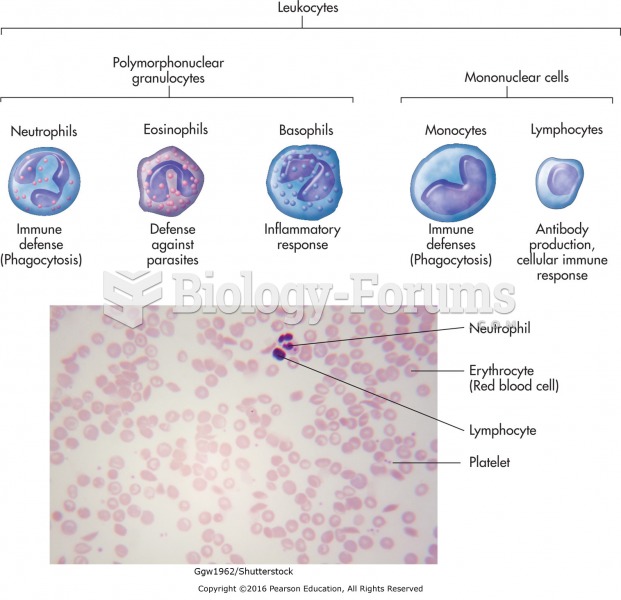
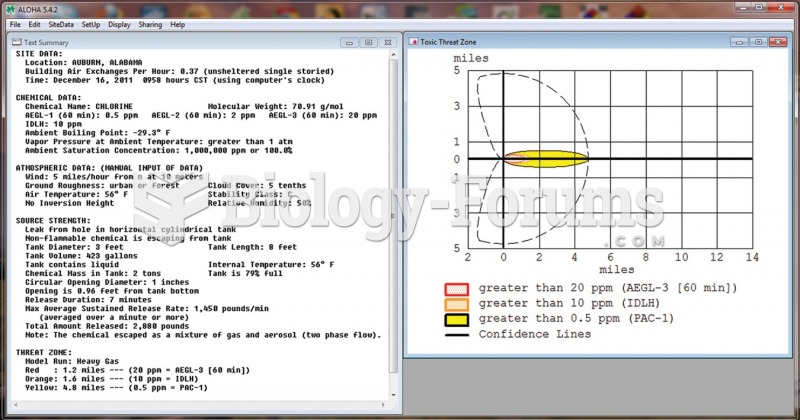
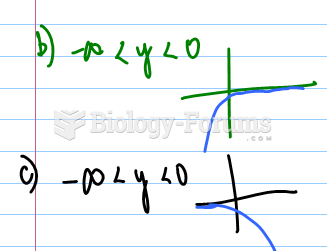
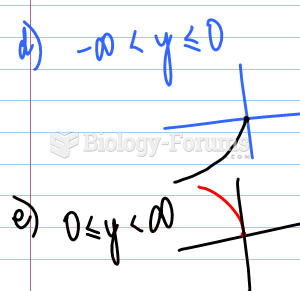This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
There are more sensory neurons in the tongue than in any other part of the body.
Did you know?
More than 4.4billion prescriptions were dispensed within the United States in 2016.
Did you know?
The first war in which wide-scale use of anesthetics occurred was the Civil War, and 80% of all wounds were in the extremities.
Did you know?
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.
Did you know?
The term pharmacology is derived from the Greek words pharmakon("claim, medicine, poison, or remedy") and logos ("study").