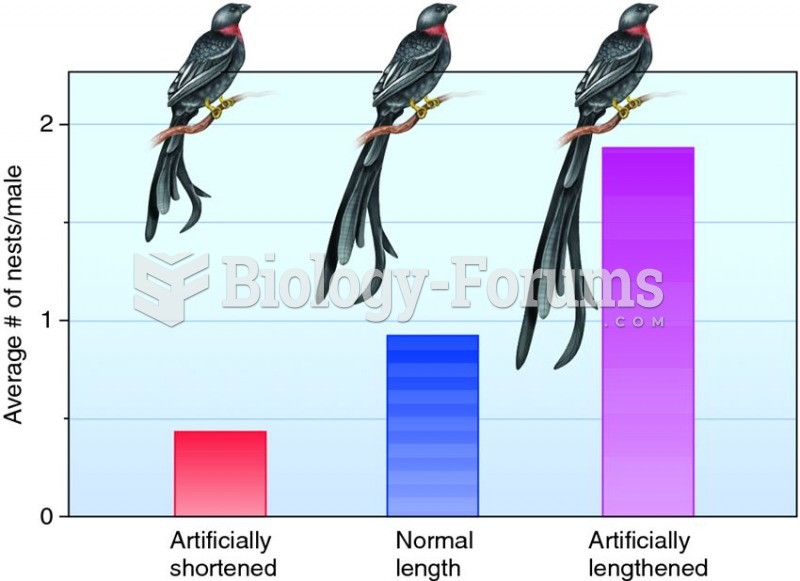
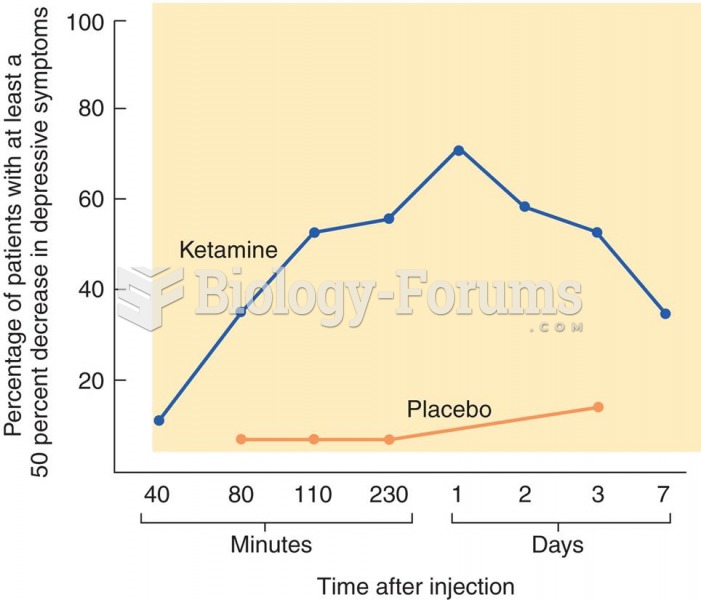
|
|
|
Eat fiber! A diet high in fiber can help lower cholesterol levels by as much as 10%.
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
Every flu season is different, and even healthy people can get extremely sick from the flu, as well as spread it to others. The flu season can begin as early as October and last as late as May. Every person over six months of age should get an annual flu vaccine. The vaccine cannot cause you to get influenza, but in some seasons, may not be completely able to prevent you from acquiring influenza due to changes in causative viruses. The viruses in the flu shot are killed—there is no way they can give you the flu. Minor side effects include soreness, redness, or swelling where the shot was given. It is possible to develop a slight fever, and body aches, but these are simply signs that the body is responding to the vaccine and making itself ready to fight off the influenza virus should you come in contact with it.
You should not take more than 1,000 mg of vitamin E per day. Doses above this amount increase the risk of bleeding problems that can lead to a stroke.
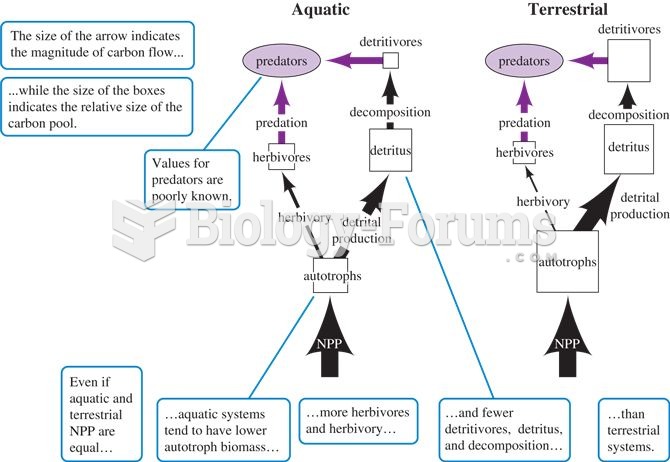 General differences in food webs and carbon flow among terrestrial and aquatic ecosystems (adapted f
General differences in food webs and carbon flow among terrestrial and aquatic ecosystems (adapted f
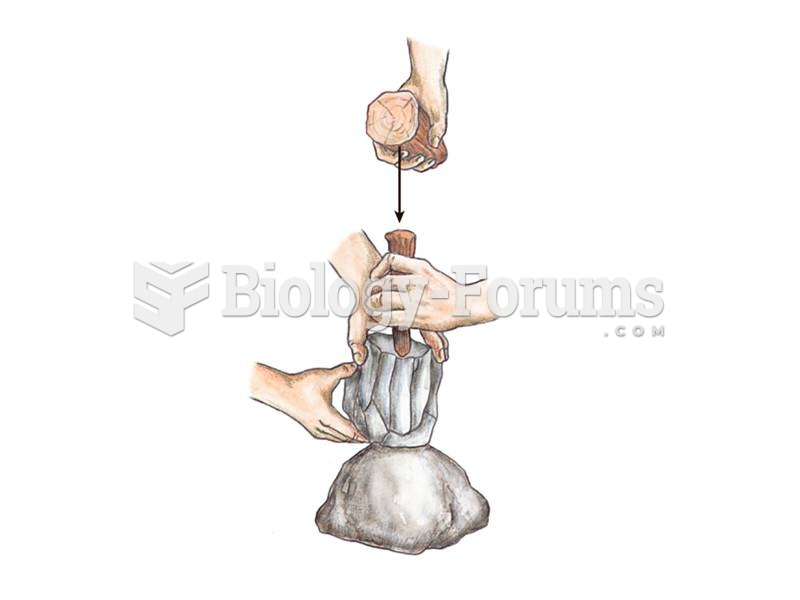 Upper Paleolithic stone tools include blade-based tools as seen here being produced from a blade cor
Upper Paleolithic stone tools include blade-based tools as seen here being produced from a blade cor