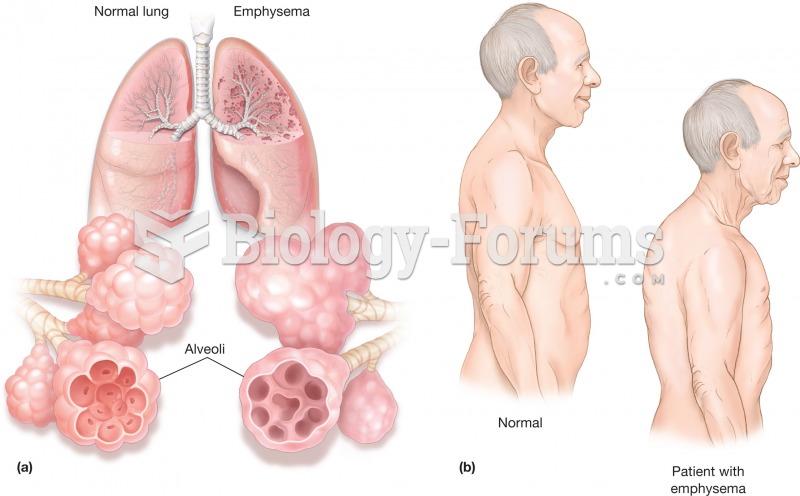
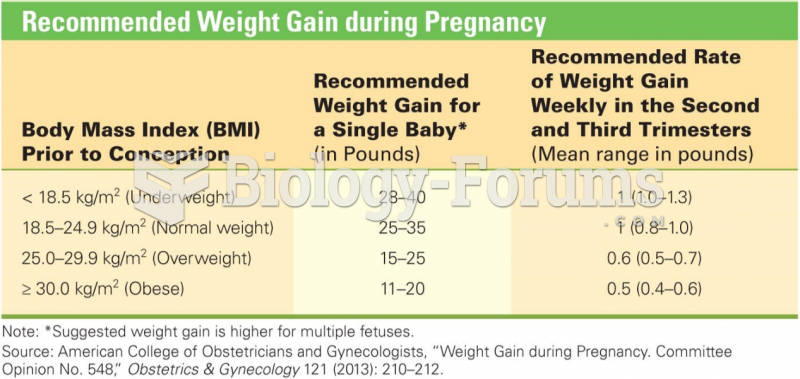
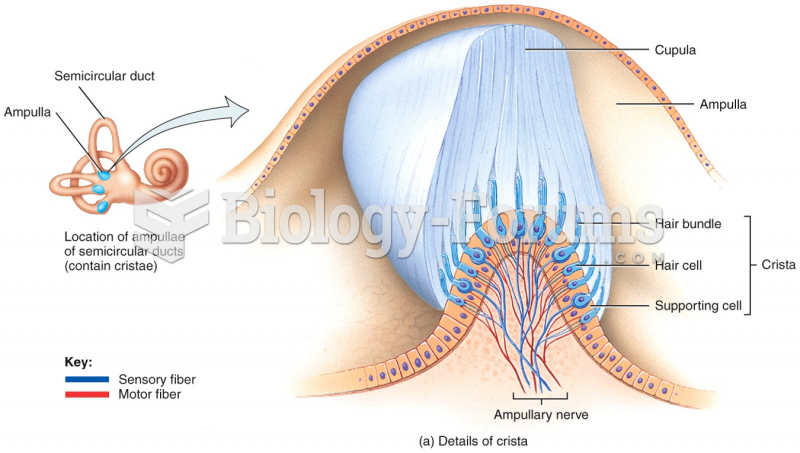
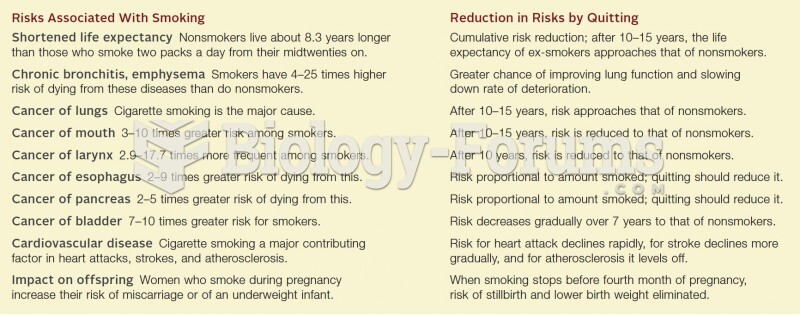
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
If you could remove all of your skin, it would weigh up to 5 pounds.
Did you know?
There are more bacteria in your mouth than there are people in the world.
Did you know?
Asthma cases in Americans are about 75% higher today than they were in 1980.
Did you know?
The immune system needs 9.5 hours of sleep in total darkness to recharge completely.
Did you know?
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).