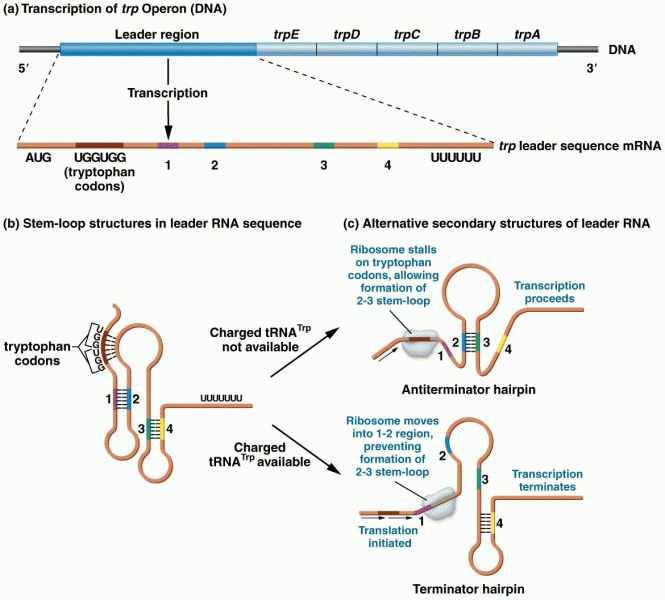
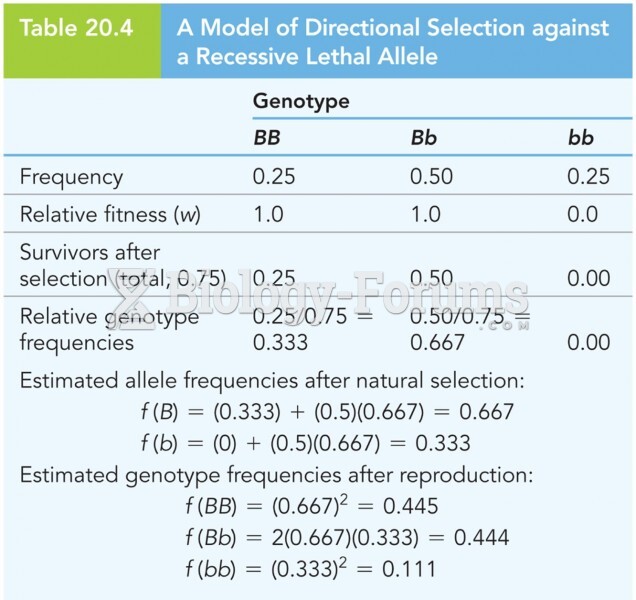
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Blood is approximately twice as thick as water because of the cells and other components found in it.
Did you know?
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
Did you know?
On average, someone in the United States has a stroke about every 40 seconds. This is about 795,000 people per year.
Did you know?
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
Did you know?
For pediatric patients, intravenous fluids are the most commonly cited products involved in medication errors that are reported to the USP.