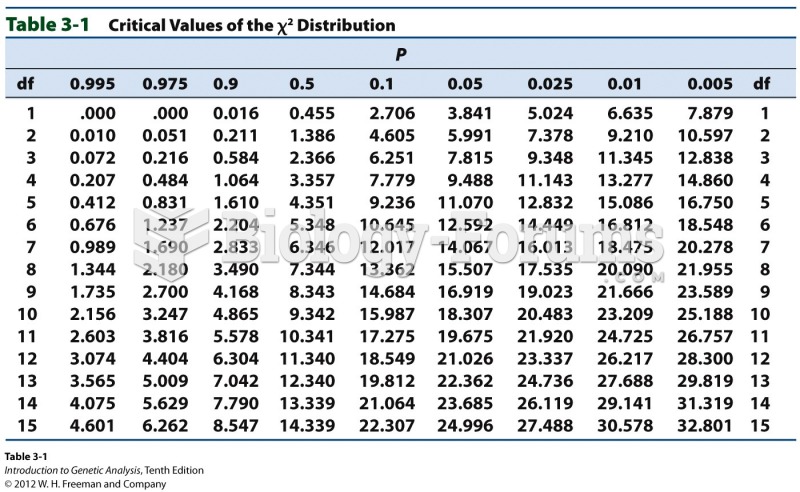
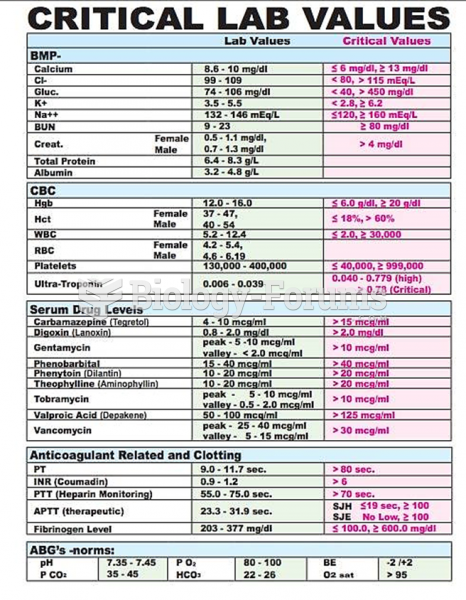
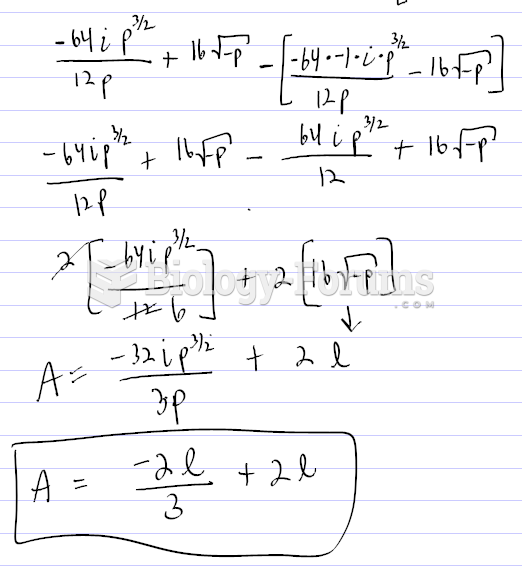
|
|
|
Never take aspirin without food because it is likely to irritate your stomach. Never give aspirin to children under age 12. Overdoses of aspirin have the potential to cause deafness.
More than 20 million Americans cite use of marijuana within the past 30 days, according to the National Survey on Drug Use and Health (NSDUH). More than 8 million admit to using it almost every day.
Since 1988, the CDC has reported a 99% reduction in bacterial meningitis caused by Haemophilus influenzae, due to the introduction of the vaccine against it.
Pubic lice (crabs) are usually spread through sexual contact. You cannot catch them by using a public toilet.
Not getting enough sleep can greatly weaken the immune system. Lack of sleep makes you more likely to catch a cold, or more difficult to fight off an infection.