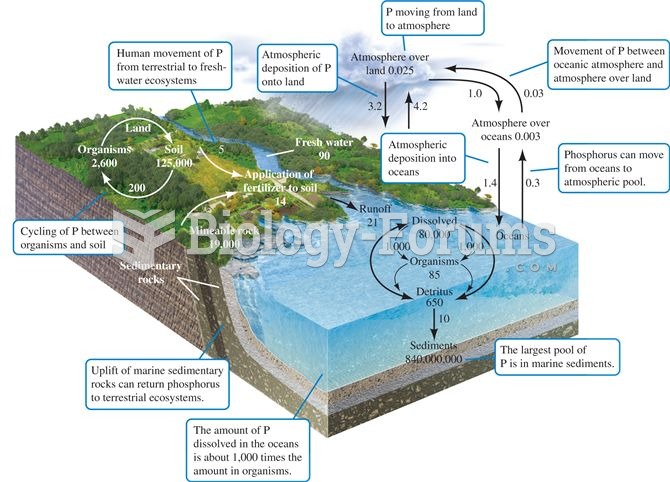
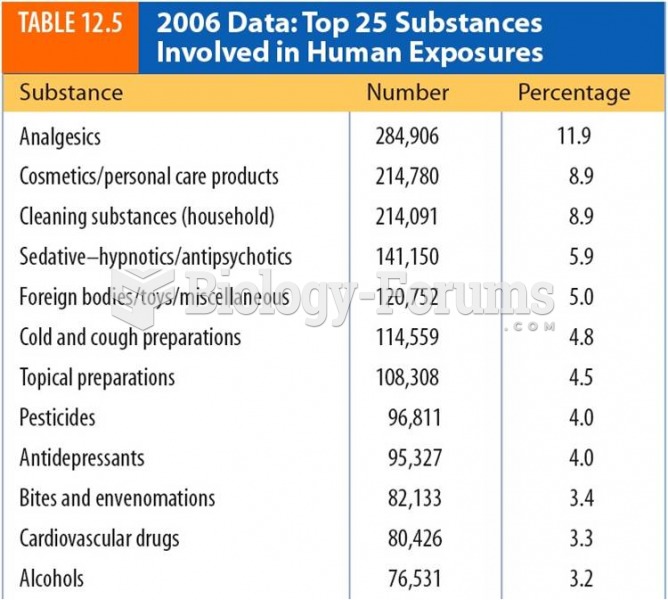
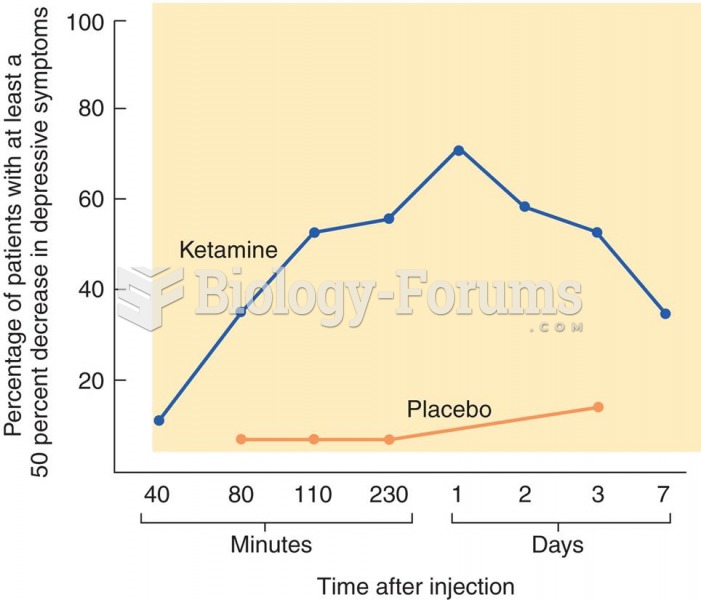
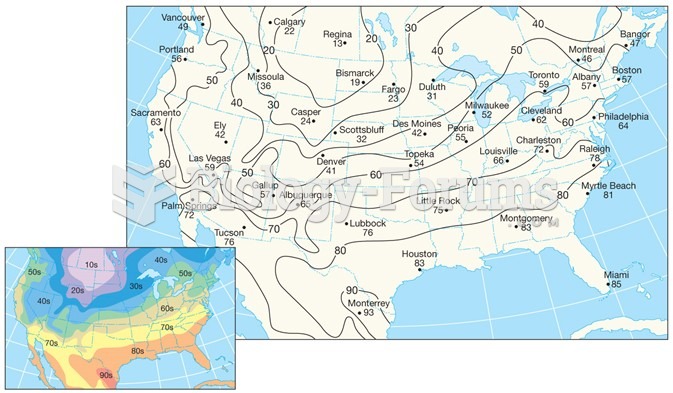
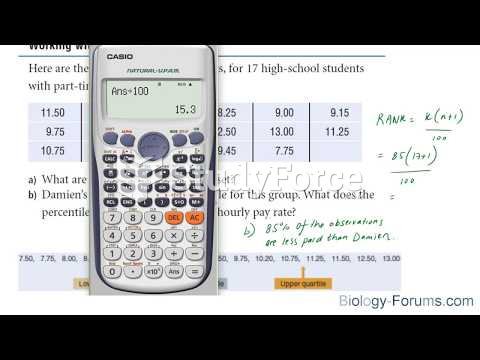
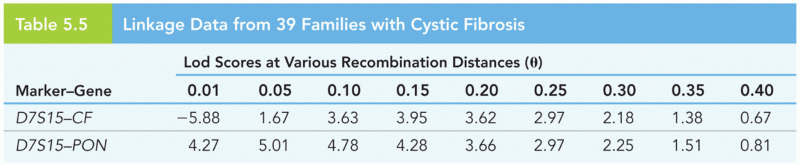
|
|
|
In inpatient settings, adverse drug events account for an estimated one in three of all hospital adverse events. They affect approximately 2 million hospital stays every year, and prolong hospital stays by between one and five days.
Most fungi that pathogenically affect humans live in soil. If a person is not healthy, has an open wound, or is immunocompromised, a fungal infection can be very aggressive.
Pregnant women usually experience a heightened sense of smell beginning late in the first trimester. Some experts call this the body's way of protecting a pregnant woman from foods that are unsafe for the fetus.
Aspirin may benefit 11 different cancers, including those of the colon, pancreas, lungs, prostate, breasts, and leukemia.
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.