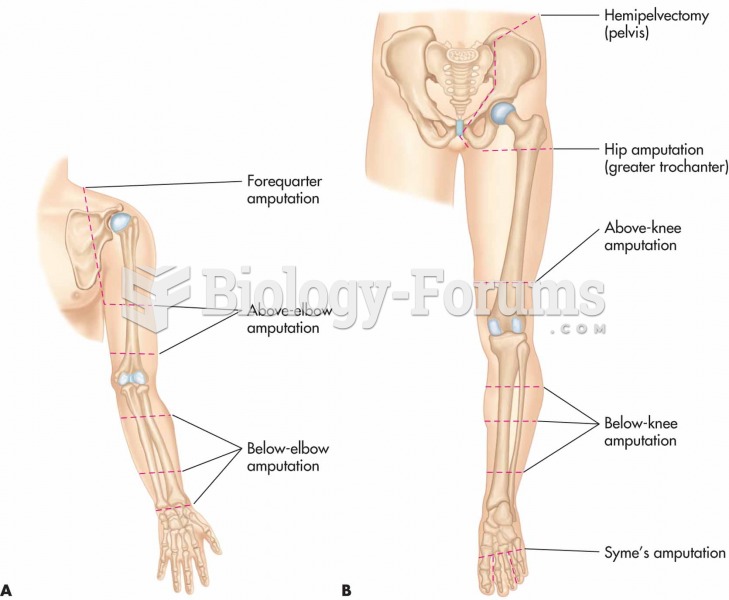
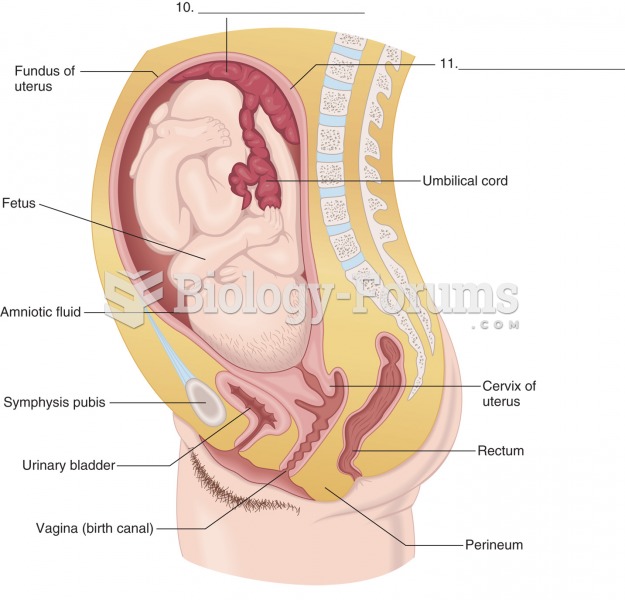
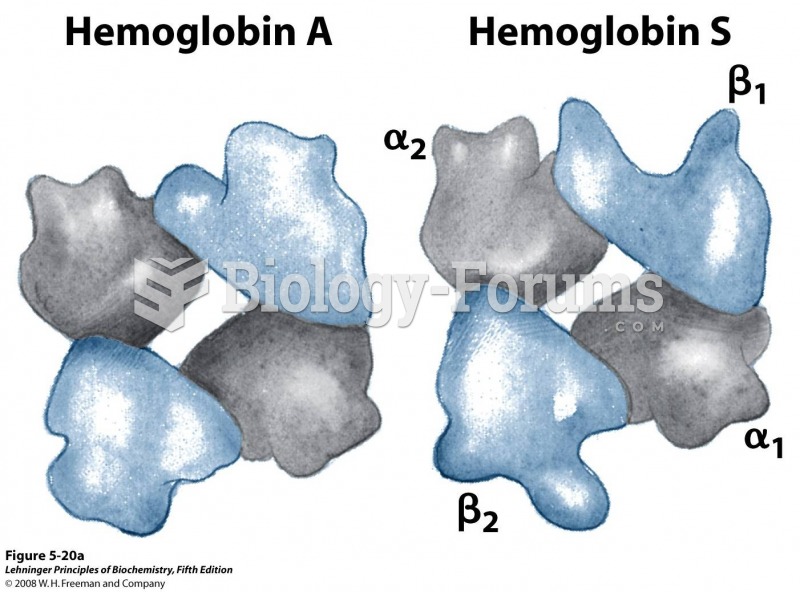
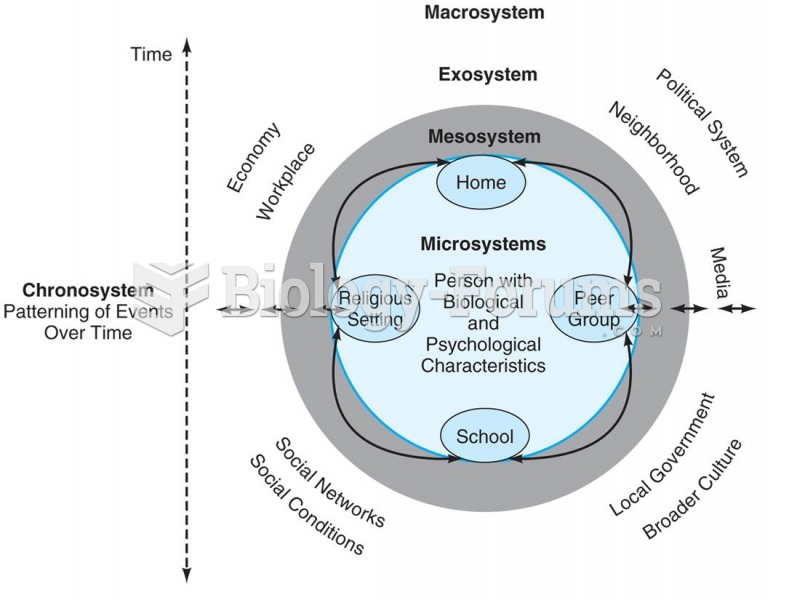
|
|
|
About 100 new prescription or over-the-counter drugs come into the U.S. market every year.
Serum cholesterol testing in adults is recommended every 1 to 5 years. People with diabetes and a family history of high cholesterol should be tested even more frequently.
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.
An identified risk factor for osteoporosis is the intake of excessive amounts of vitamin A. Dietary intake of approximately double the recommended daily amount of vitamin A, by women, has been shown to reduce bone mineral density and increase the chances for hip fractures compared with women who consumed the recommended daily amount (or less) of vitamin A.
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.