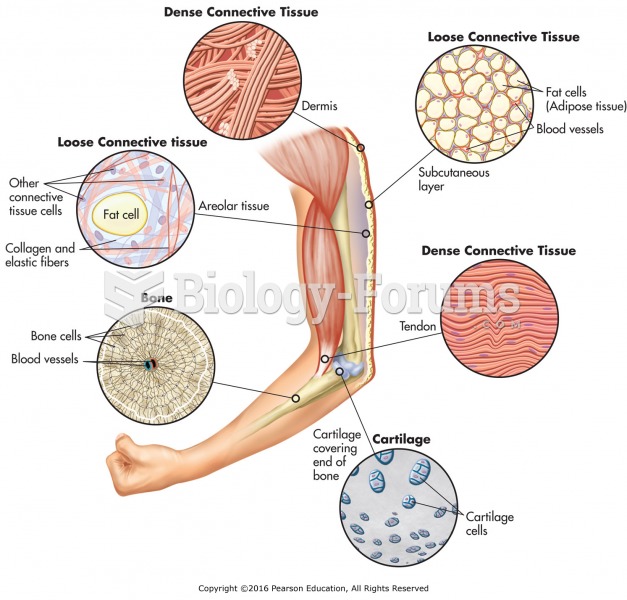
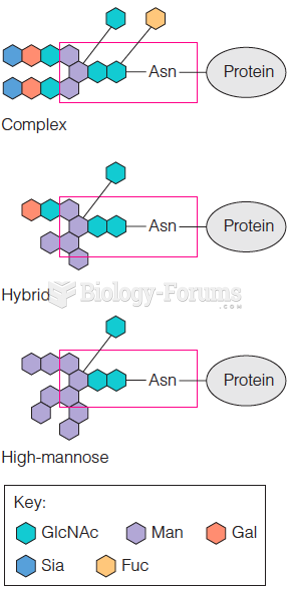
|
|
|
Vampire bats have a natural anticoagulant in their saliva that permits continuous bleeding after they painlessly open a wound with their incisors. This capillary blood does not cause any significant blood loss to their victims.
The average office desk has 400 times more bacteria on it than a toilet.
Fewer than 10% of babies are born on their exact due dates, 50% are born within 1 week of the due date, and 90% are born within 2 weeks of the date.
Women are two-thirds more likely than men to develop irritable bowel syndrome. This may be attributable to hormonal changes related to their menstrual cycles.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.